One of my first tasks as a cybersecurity researcher was analyzing results from surveys TruSecure (later Cybertrust then Verizon) conducted in the aftermath of major internet worm events of the early 2000s. While the focus wasn’t on third-party risk or supply chain risk, those themes became very apparent to me from examining the open-ended “comments” field included in the survey (yes, I was/am the kind of nerd who reads the comments). Here’s a sampling:
SQL Slammer, January 2003
- “The worm took down two of our data exchange partners.”
- “A large part of the impact for us was related to the loss of access to our external trade partners/customers.”
- “Although we were not infected by Slammer, many of our partners were. This severely interfered with our work.”
- “We were cut off from partner sites when they went down.”
Blaster, August 2003
- “We were infected when a vendor hooked up his laptop to our network.”
- “We were infected by a 3rd party on our network.”
- “Blaster got in through a trusted partner network.”
- “We were infected because partners are not keeping their machines up to date with anti-virus and OS patches. This is a real problem – our IT department doesn’t have control over what they do yet we suffer the consequences of their poor practices.”
- “Our suppliers could not confirm orders.”
- “We had numerous Infected partners. This interfered with our productivity.”
MyDoom, January 2004
- “Our customers and suppliers sent it to us.”
- “It originally came in from a partner who we have a direct connection with.”
- “The major problems have been with our trading partners who have stopped allowing any outside emails to enter their system in an attempt to stop the worm’s spread. In addition, some are restricting anything with an attachment. For our business, 99% of all our email traffic includes attachments of one type or another and so our operations have basically been shut down.” “Several of our partners were infected causing numerous operational difficulties.”
Sasser, May 2004
- 17% of participants infected reported a disruption of customer computing functions (order processing, sales, marketing, etc.).
- 16% of participants infected reported a disruption of key corporate computing functions (payroll, inventory, manufacturing, etc.).
- 14% of participants infected reported a disruption of Partner network connectivity.
Those comments caught my interest, and I continued pulling on the thread in subsequent academic and industry research. In fact, my dissertation was on managing cyber risk in supply chains. To this day, I enjoy it when I have the opportunity to study this topic because the factors and trends that exacerbate this problem have continued to increase over the last 18 years.
In almost every way imaginable, we live in a hyperconnected world. This connectivity has brought many benefits to modern business models, but it has also introduced myriad challenges and risks. If you take the time to deconstruct even the simplest of business transactions, you’ll find in the mix a surprising number of parties from technical components supporting the transaction to the completed delivery of products to the customer. But what happens to all these parties when something goes wrong?
That’s ultimately the question we wanted to answer in a new research effort from the Cyentia Institute. Our recent “Tsunami” edition of the Information Risk Insights Study (IRIS) identified 50 of the largest multi-party and supply chain cyber incidents over the past several years. We wanted to understand the causes and consequences of such events from beginning to end. Tsunami draws from the same rigorous methodology in the rest of the IRIS series. We started with a huge dataset of cyber loss events, identified those that involved multiple organizations, and then researched each event to understand who was behind it, what happened, how the spillover effects propagated through the supply chain, and the financial losses for all parties involved.
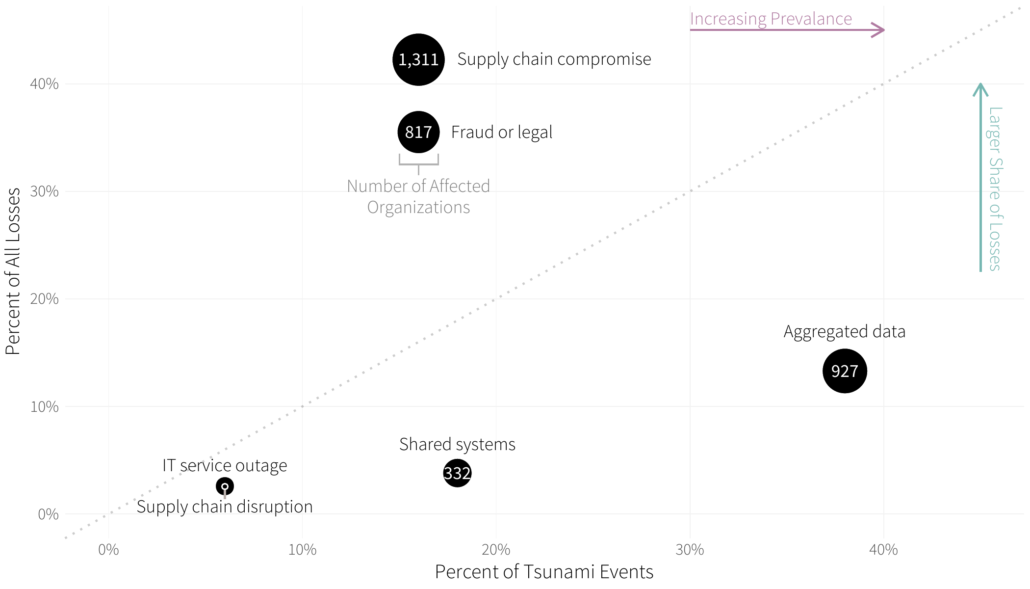
Supply chain compromise techniques used in extreme multi-party cyber incidents
I’ll share one chart from that report that goes back to how security incidents propagate to other organizations in a supply chain. Figure 8 from the Tsunami study examines the frequency and losses associated with several propagation methods. The most common form of ripple propagation that we observed is the compromise of multi-party data aggregated by the initial victim organization. The systems of downstream parties are not breached in this scenario, but those organizations nevertheless suffer various consequences as owners of the disclosed data. This is doubly unfortunate for the original data owners because they have little ability to protect the data once it has been shared. The best protection is to choose data custodians wisely and check regularly to ensure that they uphold their end of the bargain.
Ripples taking the form of supply chain compromises led to the biggest share of recorded financial losses ($7.4 billion) and the largest number of secondary victim firms. This seemed rather important, so we leveraged sub-techniques defined by MITRE’s ATT&CK to dig deeper into this ripple propagation vector. This breakdown can be found in Table 2.
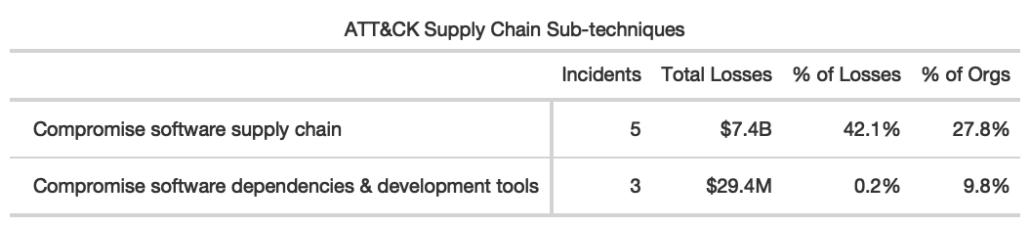
We came across no examples involving compromised hardware components moving through the supply chain prior to receipt by the end customer. Of the eight supply chain attacks we identified, five targeted software distribution mechanisms and three exploited third-party or open source software dependencies. Nearly all losses were associated with the former, and it was this sub-technique that was leveraged in the recent high-profile breaches of SolarWinds and Kaseya. The need to distribute and update code as well as leverage the benefits of third-party dependencies is fundamental to modern software development practices. Cyber adversaries, of course, are well aware of this, meaning this trend is likely to get worse before it gets better.
I could go on – the IRIS Tsunami is chock full of data and insights about mega multi-party and supply chain cyber incidents. But I think this article is already pushing the recommended post length. If interested in or responsible for managing third-party or supply chain cyber risk, I urge you to download this free report (no registration required) now. I’d be happy to hear your thoughts on things I could study on this topic over the next 18 years!







Leave a Reply
Want to join the discussion?Feel free to contribute!