Hey, you got multi-party incidents in my extreme events! You got extreme events in my multi-party incidents!
Here at Cyentia, we love cooking up analysis of cyber incidents in the service of better risk decisions. We’ve explored multi-party incidents (Ripples Across the Risk Surface) and extreme events (IRIS Xtreme) before. It’s only natural to wonder about the overlap of these dimensions. And that’s before considering recent fears about supply chain risk. That’s the purpose of our latest entry to the IRIS series: Tsunami (downloadable here).
We identified 50 of the largest multi-party cyber incidents over the past several years to understand their causes and consequences from beginning to end. We won’t cover all the juicy details here; that’s what the report is for. (Including detailed tables in the appendix–data nerds, we see you!) Instead, let’s focus on some practical implications of the research.
Now, when you say “big”…
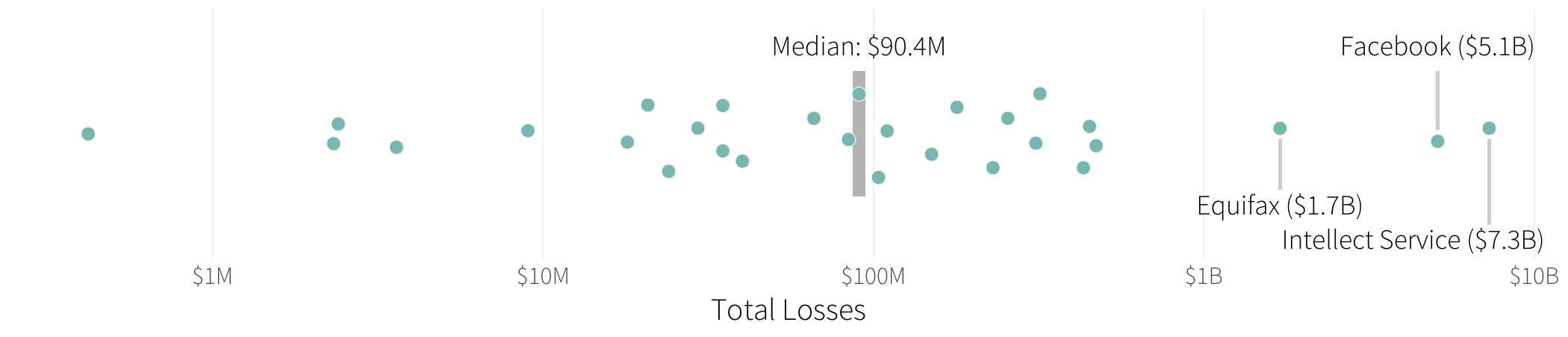
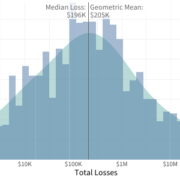
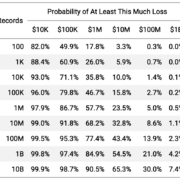
Only one event floated into the top three for more than one measurement of “big”. For reference, the three measurements were total losses, affected records, and secondary victims. So there’s a fair-to-middling chance that your definition of a “megabreach” (the SI unit for 1,000,000 breaches, I guess?) wouldn’t necessarily match someone else’s. But, does that matter? In a word, yes.
Preventive and mitigation priorities differ when you’re more concerned about affected records than, say, compromised downstream partners. And risk management programs are often heavy on considerations of direct targeting, but light on scenarios of incoming or outgoing collateral damage. Here are some ideas for when it comes time–or now; now is good–to supply chainify your risk analyses and mitigation strategy.
Avoid becoming the central victim of an extreme multi-party cyber incident.
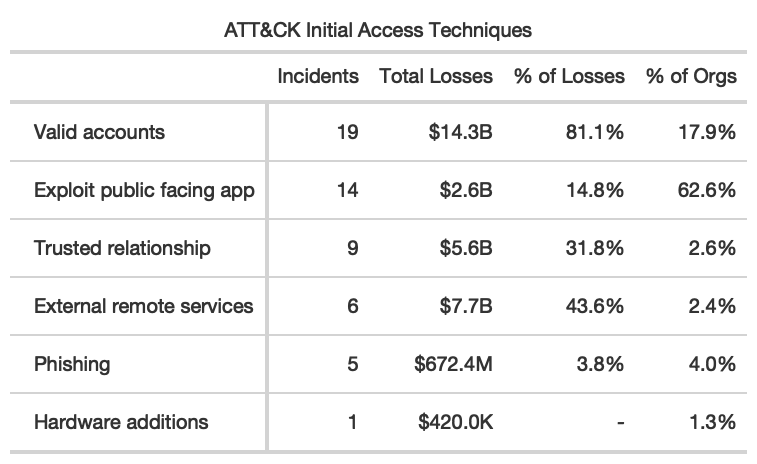
Even the largest multi-party cyber events follow well-worn paths for compromising a central victim–credentials and external web apps topping the charts. This is great(-ish) news! You don’t need to develop a new plan from whole cloth to deal with these high magnitude events.
…but, as we learned when investigating ripple events more generally, a typical ripple is ten times (10x) more expensive than a typical single-party event. Also, central victims amass nearly two-thirds of the losses when it comes to ripples.
Avoid becoming a secondary victim of an extreme multi-party cyber incident.
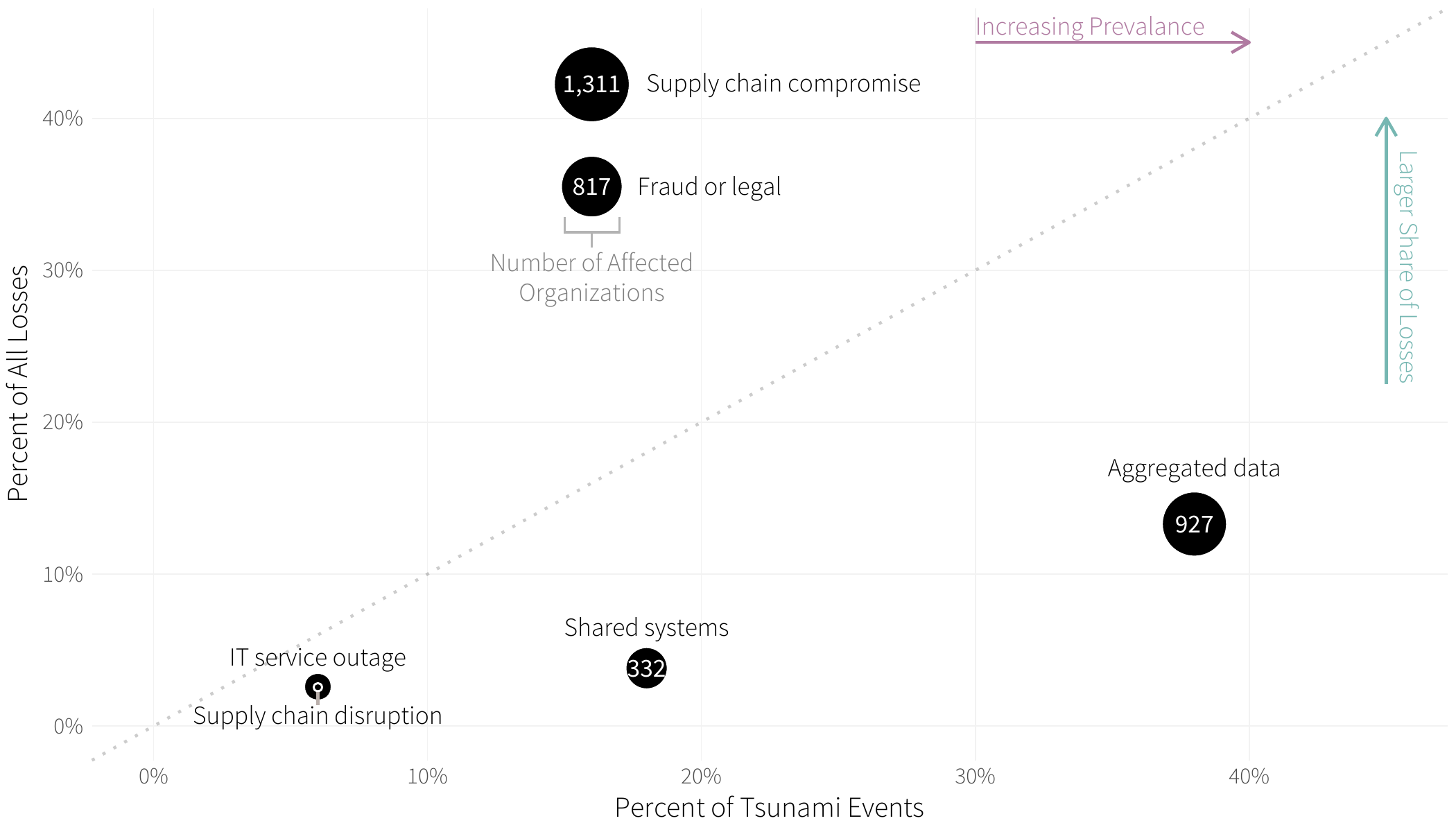
Your partners can’t lose your data if you never share it with them, right? Memes aside, spend a little extra effort up front minimizing what gets shared with partners and dig into their storage and retention practices. You’re better off preempting unnecessary exposure than relying on external validation after the fact.
The issue of software supply chain compromise (#1 by losses and secondary victims) is particularly fascinating. Security teams have toiled for years to advocate for updating software as soon as possible. Now they get an opportunity to add some nuance to the decision-making process.
If you’re dealing with high profile commercial software that has a massive customer base (read: attack surface), that advice still stands. But with more specialized applications, it’s probably safe enough to pump the brakes while you test updates in your environment. Unfortunately, these kinds of attacks have so far affected exactly the kinds of small- to mid-size businesses that are reluctant to spend resources on robust testing regimens. Perhaps with the latest research in hand, you’ll be able to nudge your team somewhere closer the middle of the two extremes.
Thirsty for more?
Join our webinar, Fri, 10/29 – 12PM ET, to hear from the authors or ask questions! Register here.
And if applying the latest insights from breach data to risk management is your cup of tea, consider Risk Retina, Cyentia’s IRIS-style analysis focused on your company and the risk dimensions that matter most.





Leave a Reply
Want to join the discussion?Feel free to contribute!