Earlier this week we held our first Cyentia-branded webinar covering the release of our IRIS 20/20 Xtreme publication and the key findings from that report. We were delighted to have Derek Vadala from Visible Risk join us. There was terrific engagement from the audience. If you missed out, have no fear! We have now posted a on-demand replay of that webinar on our new YouTube channel (Hit those Like and Subscribe buttons!). We’re also including some of the questions we received during the webinar and directly from readers since the release of the report.
Q: Where can I find a copy of the report?
A: The IRIS 20/20 report is freely available for download, with no registration required, at cyentia.com/iris.
Q: Is this data available for download?
A: Yes! We’re delighted to say that not only the data behind this report, but the full data set of our collection of over 200 elements on these events is now available for subscription. Subscribers will receive an ongoing feed of not only the current data, but all updates to existing and new events. We’re already at work adding 2014 and 2020 events! Please reach out to [email protected] to discuss the particulars.
Q: Why is there no measured competitive advantage or reputational impacts on any of these events?
A: This was a surprise to us as we started acquiring data. While reputational damages and impacts to competitive advantage are often cited by risk professionals, we found no evidence of any company recording losses in these categories across these Xtreme events. This isn’t to say costs don’t exist in these categories, just that companies don’t recognize the costs in any measurable way. This matches up with the very uncertain evidence on stock price effects from breaches — there may be some effect, but it is largely not significant to most firms.
Q: How does our very low prevalence of insider abuse match up with the high prevalence of credential abuse?
We base our categorization of actions, actors, and attributes on the VERIS framework. Under these classifications, the compromise of a trusted credentials by an external actor who did not collude with an internal party, is considered external. Remember that most external attacks are focused on gaining access to internal resources. That these external actors succeed does not make them all insider abuse!
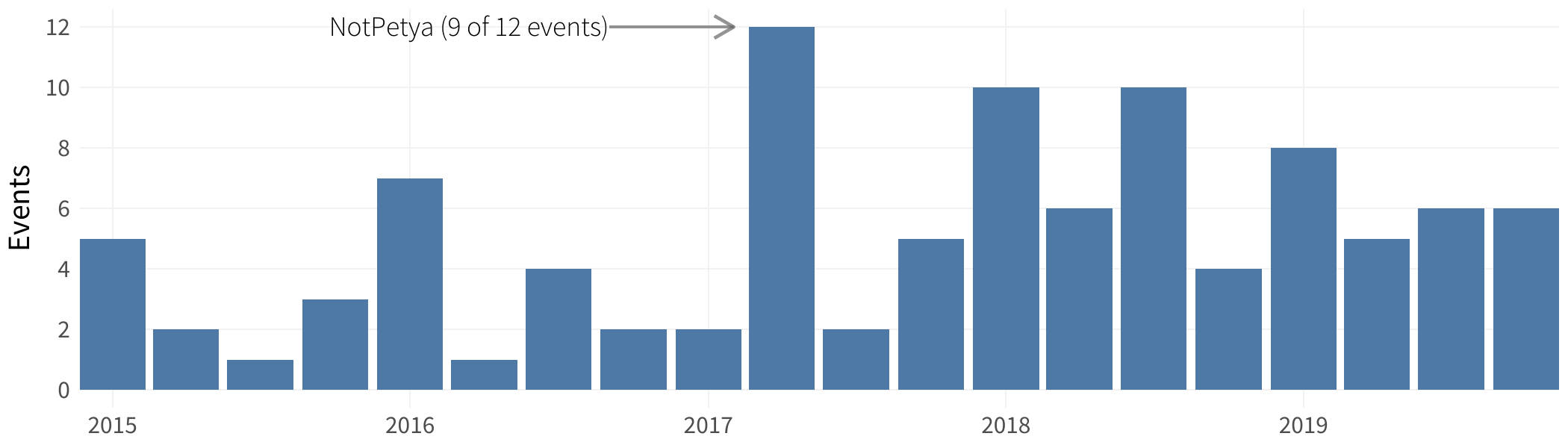
Q: You state that Xtreme events are relatively rare. Does this fit with a statistical distribution (normal, log-normal, etc.)?
A: The overall losses of all the IRIS 20/20 events fit well with a log-normal distribution. For IRIS Xtreme, we looked at the frequency of events and while there is arguably a slight upward trend in recent months, there is not a strong statistical fit. We’re continuing to maintain this data set and hope to revisit this as our data set expands.
Q: Do you break down the category of loss for every event?
A: Our approach in IRIS Xtreme was to look at the population of events to draw observations and guidance. Not all events have distinguishable components of loss separate from their overall losses. That said, where we do have detailed loss type information, we include that on a per event basis in the Xtreme data set now available for subscription.
Q: Are these events US only or are international events included?
A: Our scope is global. Note that due to US disclosure laws and other compliance obligations, Xtreme events affecting US-located firms are often much easier to identify and obtain information.
Q: Are the categories and patterns of activity mutually exclusive? Can there be, for example, both phishing and ransomware?
A: Similar to work in the Verizon DBIR and in VERIS, categories are not mutually exclusive. It is possible for events to have multiple perspectives. Rather than forcing events into a single category, we tally the most crucial categories for a more complete picture.
Q: There is discussion about the impact of SEC filings and ransomware on Xtreme events. How can I explore that in more detail?
A: Below we have an interactive plot that can allow you to explore this data in more detail. For further investigation, please reach out to [email protected] to discuss subscribing to the full data feed.






Leave a Reply
Want to join the discussion?Feel free to contribute!