/wp-content/uploads/2024/04/State-of-TPRM-report-2024_Cover.jpg
1920
1484
Carolyn Gimarelli
/wp-content/uploads/[email protected]
Carolyn Gimarelli2024-05-16 12:00:272024-05-16 10:54:47The State of Third-Party Risk Management with Risk Recon
/wp-content/uploads/2024/03/calendar-forblog.png
900
2100
Jay Jacobs
/wp-content/uploads/[email protected]
Jay Jacobs2024-03-15 13:13:072024-03-15 23:25:08Call for Sponsors: Inaugural Exploit Prediction Annual Report
/wp-content/uploads/2023/11/fig13.png
1200
1500
Carolyn Gimarelli
/wp-content/uploads/[email protected]
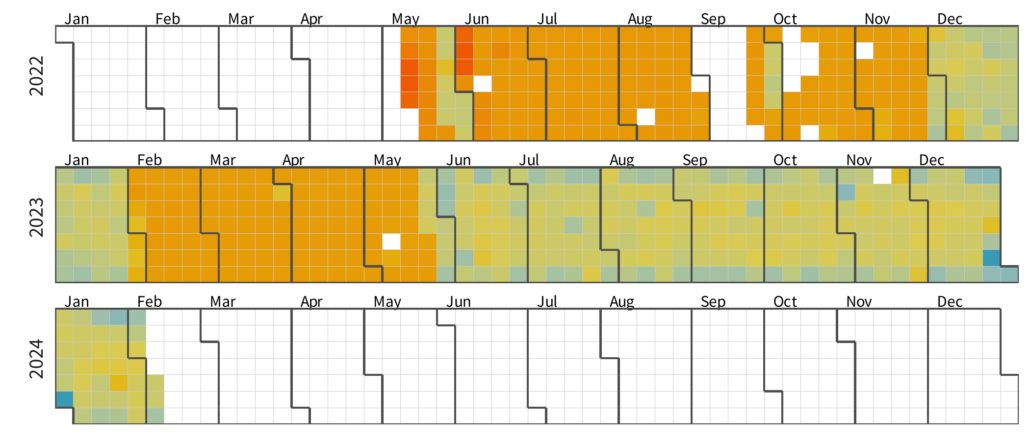
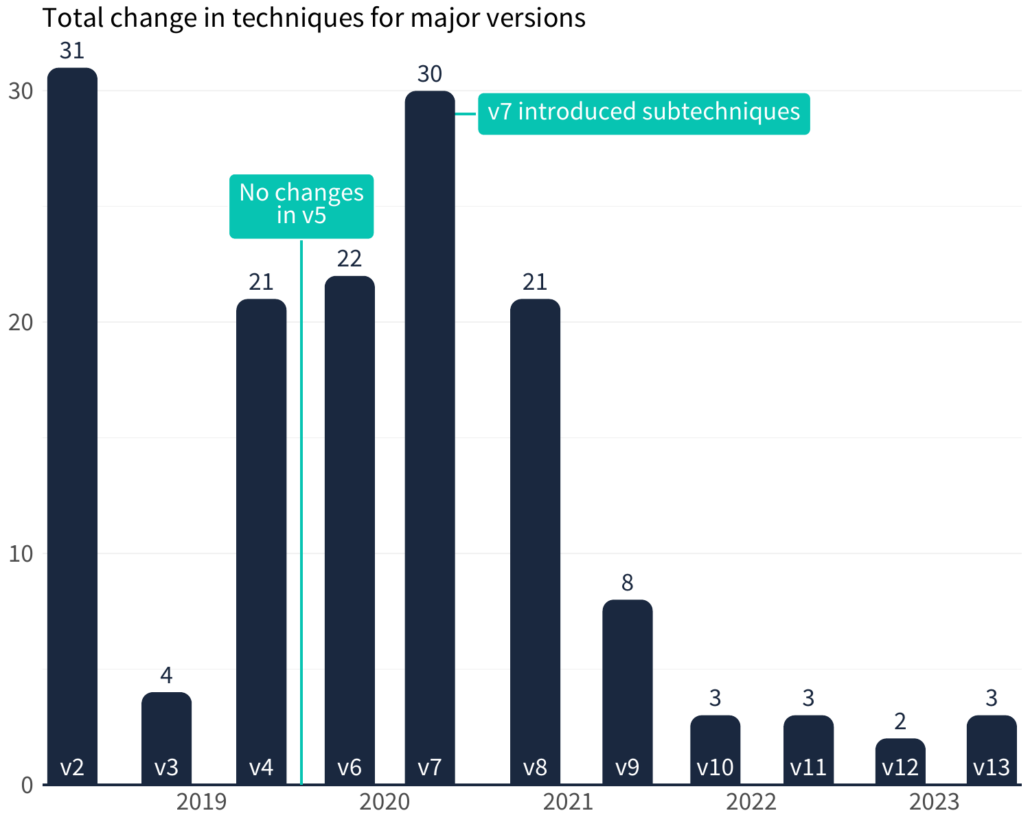
Carolyn Gimarelli2023-11-27 12:15:372023-11-21 20:02:53Exploring Insights from "Multi-Source Analysis of Top MITRE ATT&CK Techniques"
/wp-content/uploads/2023/09/IRIS-T-Fig7-1-1.jpg
900
1600
Carolyn Gimarelli
/wp-content/uploads/[email protected]
Carolyn Gimarelli2023-09-29 12:20:062023-10-20 11:08:30We spill the Tea on Threat Event Analysis!
/wp-content/uploads/2023/09/IRISTEA_MU2-2-1.png
1920
1712
Carolyn Gimarelli
/wp-content/uploads/[email protected]
Carolyn Gimarelli2023-09-29 12:15:062023-10-20 11:08:11Press Release: Information Risk Insights Study (IRIS) Risk Retina® Threat Event Analysis
/wp-content/uploads/2023/08/P2P-Cover.jpg
792
612
Carolyn Gimarelli
/wp-content/uploads/[email protected]
Carolyn Gimarelli2023-08-07 17:28:132023-08-18 11:43:26Prioritization to Prediction, Vol. 9: Role of the known exploited vulnerability catalog in risk-based vulnerability management
/wp-content/uploads/2023/08/Square-IRIS.jpg
1080
1080
Carolyn Gimarelli
/wp-content/uploads/[email protected]
Carolyn Gimarelli2023-06-26 12:15:152023-10-20 11:24:04Strengthening Healthcare Security: Optimizing Vulnerability Remediation with IRIS Risk Retina
/wp-content/uploads/2023/05/SSC-AVD-MU-2.png
1281
1920
Carolyn Gimarelli
/wp-content/uploads/[email protected]
Carolyn Gimarelli2023-06-05 12:15:352023-06-21 16:23:57New Research: Close Encounters of the Third & Fourth Party Kind Subsector Reports
/wp-content/uploads/2023/05/Intro-3.jpg
900
1600
Carolyn Gimarelli
/wp-content/uploads/[email protected]
Carolyn Gimarelli2023-06-01 08:00:332023-05-31 13:50:10New Research: Balancing Third-Party Risk
/wp-content/uploads/2023/05/Screenshot-2023-05-17-at-9.20.48-AM.png
980
1832
Wade Baker
/wp-content/uploads/[email protected]
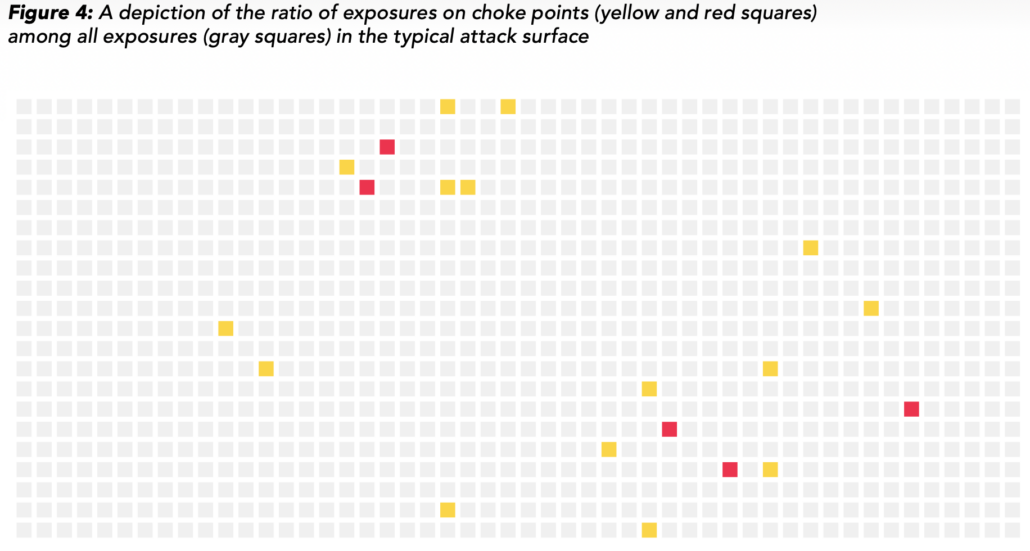
Wade Baker2023-05-25 12:15:502023-05-26 17:05:25Visualizing the Value of Attack Path Choke Points for Prioritization
© Copyright 2024 Cyentia Institute
Scroll to top