One pivotal question echoes amongst the cyber community: “How will adversaries attack us, and what defenses should we prioritize?” This inquiry propels the industry’s quest for insights within the ever-shifting threat landscape. MITRE ATT&CK®, a beacon of knowledge, guides this journey with its repository of adversary tactics and techniques gleaned from real-world observations.
However, amidst the wealth of statistics on ATT&CK techniques dispersed across diverse cybersecurity reports, distilling consensus proves challenging. In response, our collaborative study with Tidal Cyber meticulously scrutinizes 22 public sources with the aim of consolidating a unified perspective on the top ATT&CK techniques from diverse sources, providing a foundation for a more informed defense against threats. While we successfully achieved this objective, the journey presented several hurdles that we feel are important to share. Our hope is that these insights contribute to enhancing the accuracy and usefulness of reported information and guide others involved in similar analyses.
Security professionals confront a myriad of challenges, including the rapid pace of updates, the ambiguity of tactic-technique relationships, the under-reporting of sub-techniques, and a lack of reporting tailored to specific segments. The exploration begins with a comprehensive investigation into source visibility and reporting across the ATT&CK matrix. Are our sources casting a wide net, observing a multitude of techniques, or are there discernible blind spots?
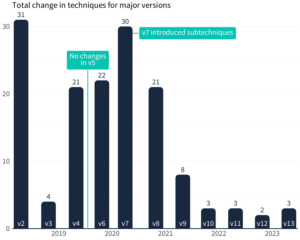
The ATT&CK matrix is far from static. Annual major versions bring about significant changes, and while the alterations were substantial a few years ago, the pace has steadied in recent years. This evolution indicates ATT&CK’s progress into a more stable state, facilitating reporting and analysis. Nevertheless, versioning challenges persist due to the lack of distinction in sources regarding the ATT&CK version in use.
While the situation has improved, sources seldom specify the version, necessitating manual translation to ensure accuracy. It’s crucial to verify the validity of techniques and sub-techniques from public reports to prevent the propagation of discrepancies.
A common misconception among those new to ATT&CK is the assumption that all techniques align with just one tactic. However, closer inspection reveals a more nuanced reality—there isn’t a straightforward 1:1 relationship. While not extreme, this variance across the enterprise ATT&CK matrix introduces analytical challenges that require careful navigation.
Most sources aggregate observations at the individual technique level rather than detailing tactic-technique pairings. To alleviate this challenge, reporting organizations are encouraged to explicitly highlight these associations, aiding defenders in interpreting and applying this valuable information effectively.
Get the full analysis in “Multi-Source Analysis of Top MITRE ATT&CK Techniques” where we cover these challenges in detail as well as the analysis on the most reported ATT&CK TTP, the most frequent ATT&CK techniques and more!
Want even more? Watch the replay where Wade Baker and Frank Duff Examine more details from the new report!




Leave a Reply
Want to join the discussion?Feel free to contribute!