We at Cyentia Institute had the opportunity to analyze data from millions of attack path assessments conducted by XM Cyber over the last year. I’d like to share a chart from the report we published from that analysis because it touches on a theme I love exploring in cybersecurity management: prioritizing remediation.
Choke Points: From Concept to Data
We found that the typical organization has 11,000 security exposures that attackers could exploit. These are denoted by the gray squares in the figure, each of which represents 10 exposures. The vast majority of exposures are dead ends or don’t put critical assets at risk, which is why we’ve grayed them out.
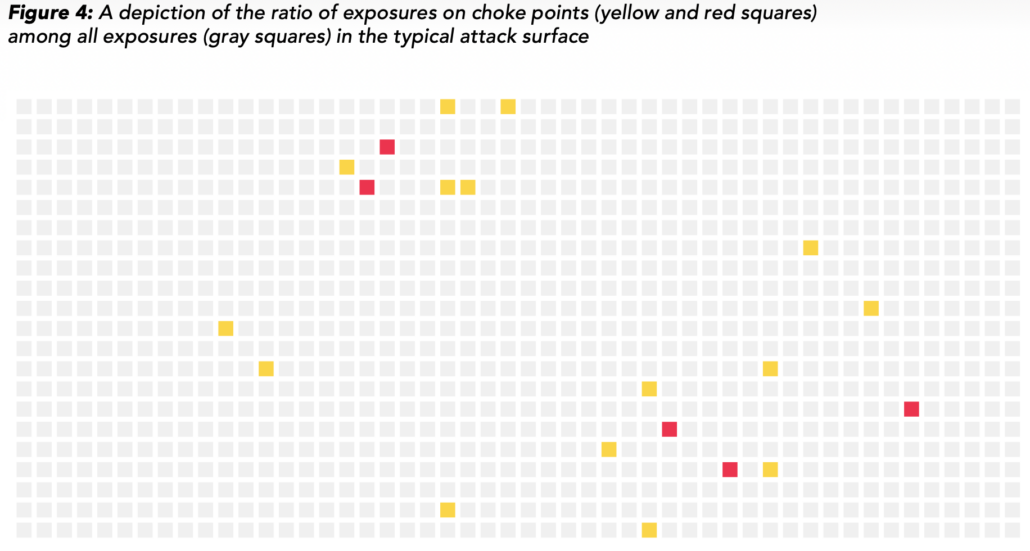
About 2% (~200) of these exposures are located on choke points – entities through which multiple attack paths converge en route to critical assets. These “choke points” are colored yellow and red (more on that distinction in a moment). If you’re looking for quick wins to reduce substantial risk, these offer compelling focal points.
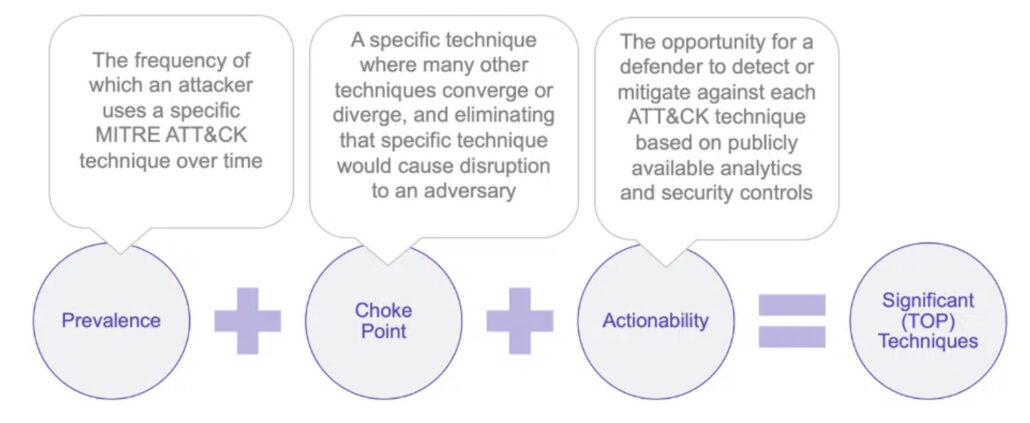
Before we had the chance to examine this data, choke points were just an abstract concept to me. I first recall seeing that term in relation to the MITRE ATT&CK projects that include the visual below. But I don’t recall ever seeing any data on the prevalence of chokepoints or common types of them.
Back to the data at hand, the news for beleaguered defenders gets even better! Our analysis reveals that about one in four choke points exposes 10% or more of the critical assets in the environment (red squares). In other words, these exposures put attackers on the fast track to causing major harm to the organization. Prioritizing these critical choke points represents a minimal effort, maximum effect approach that equates to a whopping 99.6% reduction in the scope of remediation!
Reflections on the Cost of Attack
As we analyzed data and reflected on the findings for this report, my mind kept coming back to one concept: the cost of attack. I’ve long been preoccupied with the concept of making it more costly for attackers to successfully compromise our organizations than the value they get from doing so. In fact, I wrote this in the very first edition of Verizon’s Data Breach Investigations Report in 2008:
“Though some movie plots would have us believe otherwise, cyber attacks in the real world rarely involve Mission Impossible-like scenarios. Quite the opposite, in fact… Given enough time, resources and inclination, criminals can breach virtually any single organization they choose. They cannot breach all organizations…Unless the value of the information to the criminal is inordinately high, it is not optimal for him to expend his limited resources on a hardened target while a softer one is available. The goal, then, is to implement security measures such that it costs the criminal more to compromise your organization than other available targets.”
2008 was a long time ago, and I’d like to think we would have reached that goal by now. But as best I can tell, we haven’t—at least not for the majority of organizations. And that’s why I’m fascinated with what we learned in this analysis based on what XM Cyber are doing through attack path analysis.
We can see what the attacker sees and identify their least costly (quickest, easiest) routes to whatever it is they value. The concept of choke points shows where we can disrupt those routes most efficiently so attackers cannot achieve their objective. If we can operationalize that knowledge, I have hope that we actually can shift the cost of attack in our favor. And that would make me very happy, indeed!
Download the full report: https://info.xmcyber.com/2023-state-of-exposure-management
View webinar recording: https://info.xmcyber.com/navigating-the-paths-of-risk-the-state-of-exposure-management-in-2023





Leave a Reply
Want to join the discussion?Feel free to contribute!