“You know when you make a copy of a copy, it’s not as sharp as the original.”
– Doug Kinney (Michael Keaton), Multiplicity
Cyentia recently released our second report in collaboration with SecurityScorecard titled “Close Encounters of the Third (and Fourth) Party Kind.” Yeah, yeah – I know that’s an obvious tee-up for a quote from that movie rather than Multiplicity, but we’ve already had some fun with that thread. Anyway, we analyzed data on the digital supply chains of 230,000 organizations to gain insights into the complex and interdependent nature of third and fourth-party relationships.
The stat that garnered the most attention was our discovery that 98% of organizations have at least one direct third party with a known breach in the last two years. Our finding that half of organizations have indirect (fourth-party) connections with at least 200 breached firms also got some coverage. But I don’t want to talk more about those today – I’d like to focus on a couple of others worth considering.
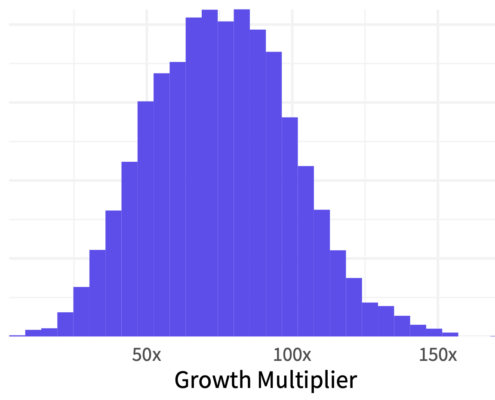 First up, we measured fourth-party multiplicity. It stands to reason that the more third parties a firm maintains, the amount of fourth-party relationships would be even greater. But I’ve never had the data to actually measure that ratio. Thanks to SecurityScorecard, we were able to do exactly that.
First up, we measured fourth-party multiplicity. It stands to reason that the more third parties a firm maintains, the amount of fourth-party relationships would be even greater. But I’ve never had the data to actually measure that ratio. Thanks to SecurityScorecard, we were able to do exactly that.
To measure this, we counted the number of third parties for each primary organization, and the total number of organizations each of those third parties was connected to (fourth parties). We then used those tallies to calculate a third-to-fourth-party growth multiplier for every organization. The chart to left depicts how this growth multiplier plays out across all firms.
Turns out, the typical organization has indirect relationships with 60 to 90 times the number of fourth parties. The fourth-party growth multiplier for most organizations ranges between 15x and 150x. Depending on your perspective, that may seem remarkably compact or incredibly wide. But either way, the primary point is that if you think keeping track of third parties is a challenge…monitoring fourth-party multiplicity is a whole other ballgame!
Perhaps you’re thinking “So what?” “Why does it matter how many fourth parties we’re indirectly connected to?” Well, we already shared one answer – there’s a good chance those third and fourth parties have been or will be breached. And if they’re accessing your systems, sharing your data (or vice versa)…that may not turn out so well.
But the report also offers another answer worth noting in the chart below. It compares the fourth-party growth factor I just talked about with the organizations’ overall security rating as assessed by SecurityScorecard. The trend is pretty clear. The fourth-party growth multiplier of organizations with a failing security grade is 10x that of those rated A. Thus, we see an inverse correlation between expansive third and fourth-party dependencies and strong security posture.
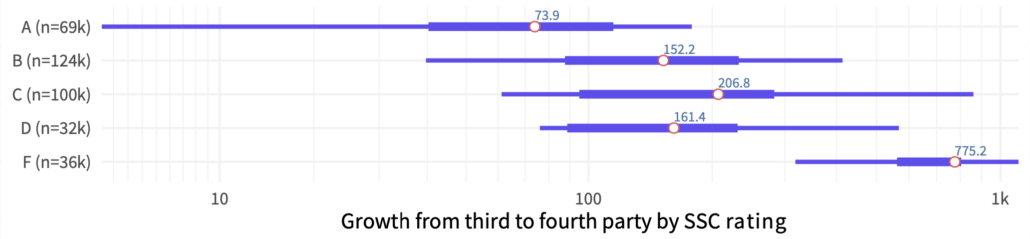
The takeaway from all this? Don’t expect security posture to be equally sharp across all parties in your supply chain. Like in the movie Multiplicity, relationships tend to get really complicated when partners begin making copies of copies.




Leave a Reply
Want to join the discussion?Feel free to contribute!