In a previous monthly webinar, we dove into the power of Exploit Intelligence Service for threat-driven remediation. As vulnerabilities continue to increase, it’s crucial to prioritize remediation efforts effectively.We explore how tracking exploit code and understanding the threat landscape can revolutionize your vulnerability management strategy.
The Need for Prioritization
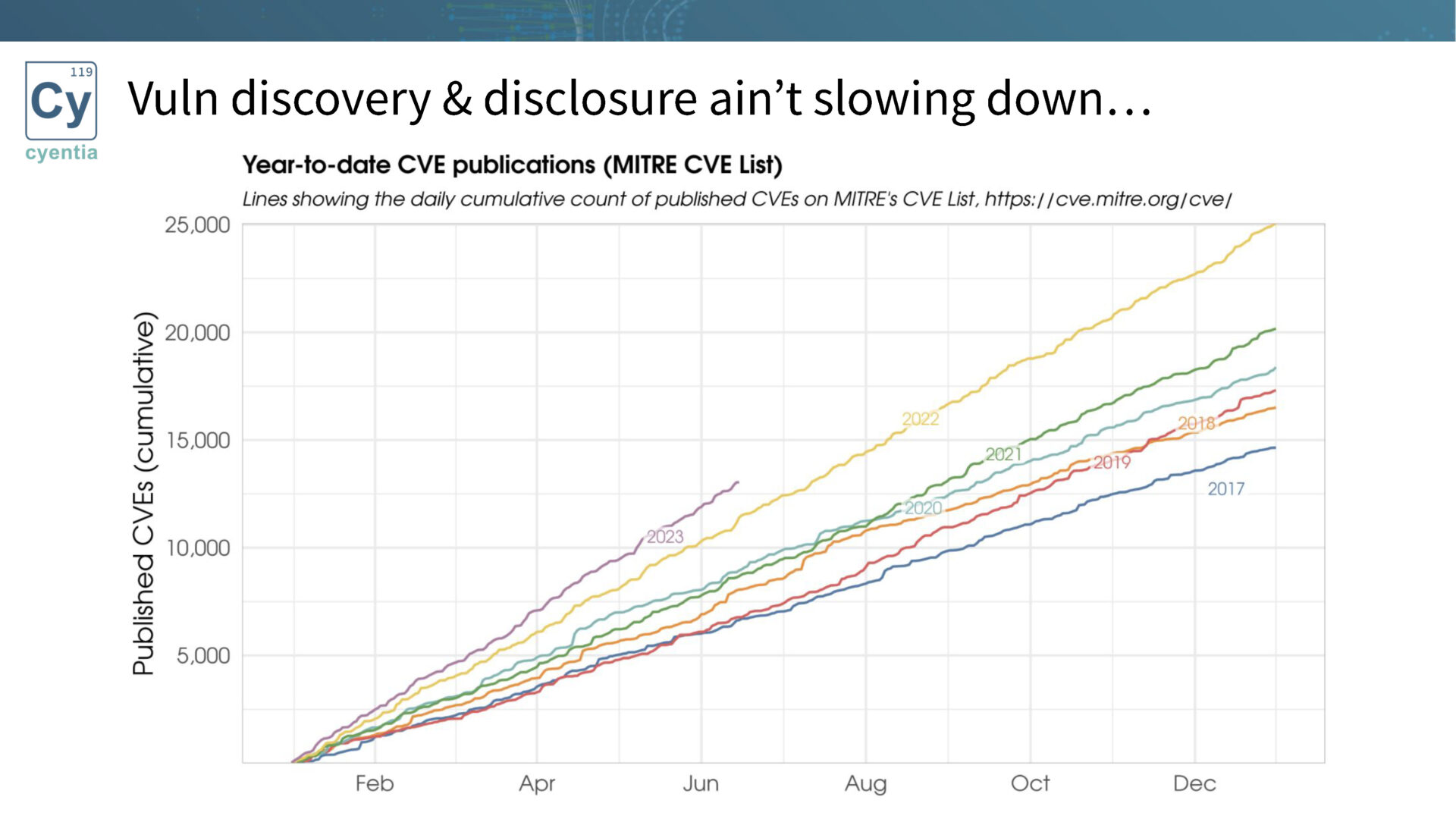
Vulnerability discovery and disclosure are on the rise, with an ever-growing number of published vulnerabilities each year. The sheer volume makes it impossible to fix all vulnerabilities, emphasizing the need for prioritization. 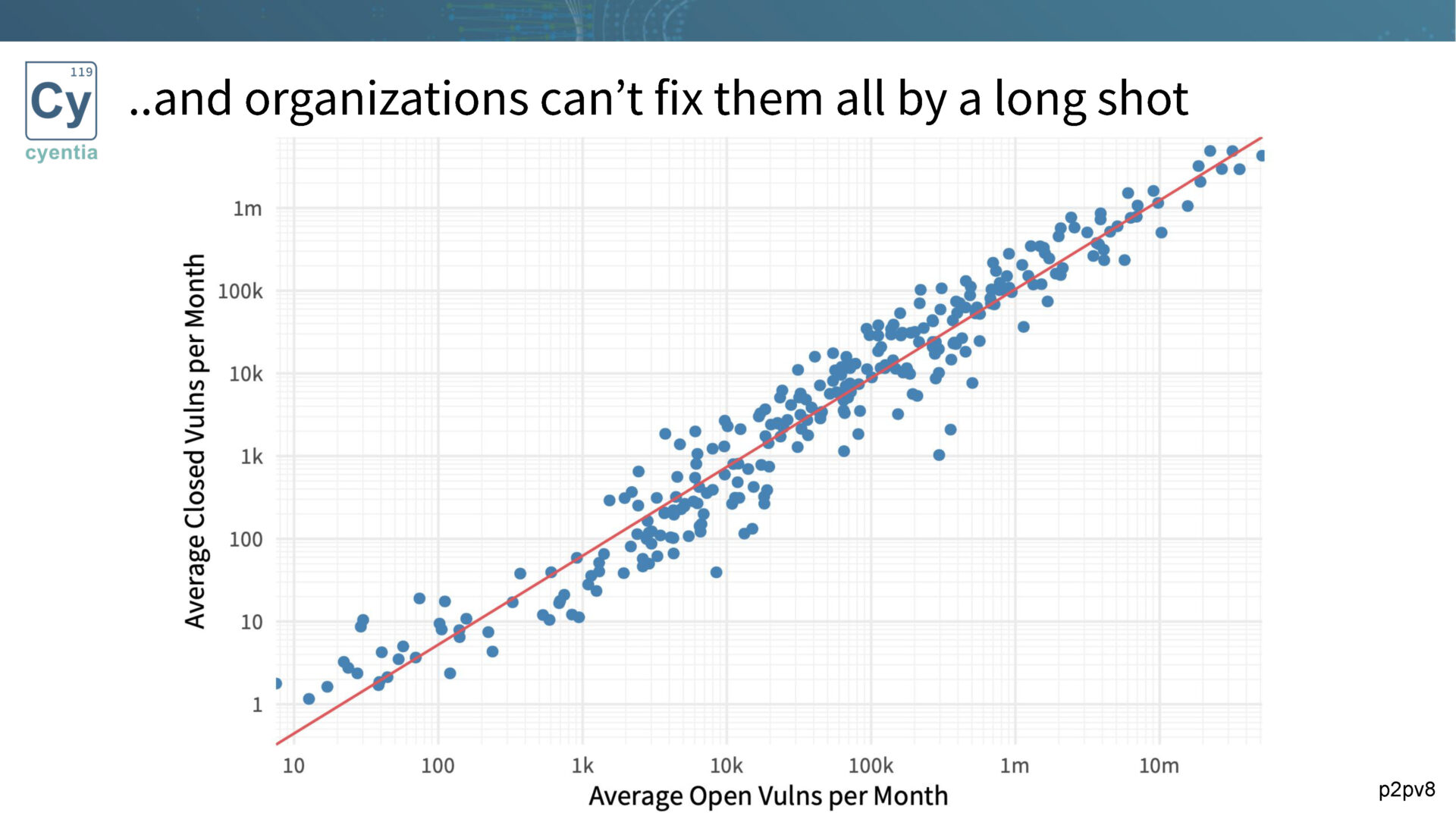
Organizations typically address only around 15% of vulnerabilities each month, underscoring the importance of determining which subset of vulnerabilities requires immediate attention.
For more information on the complexities of vulnerability remediation, check out Wade’s article.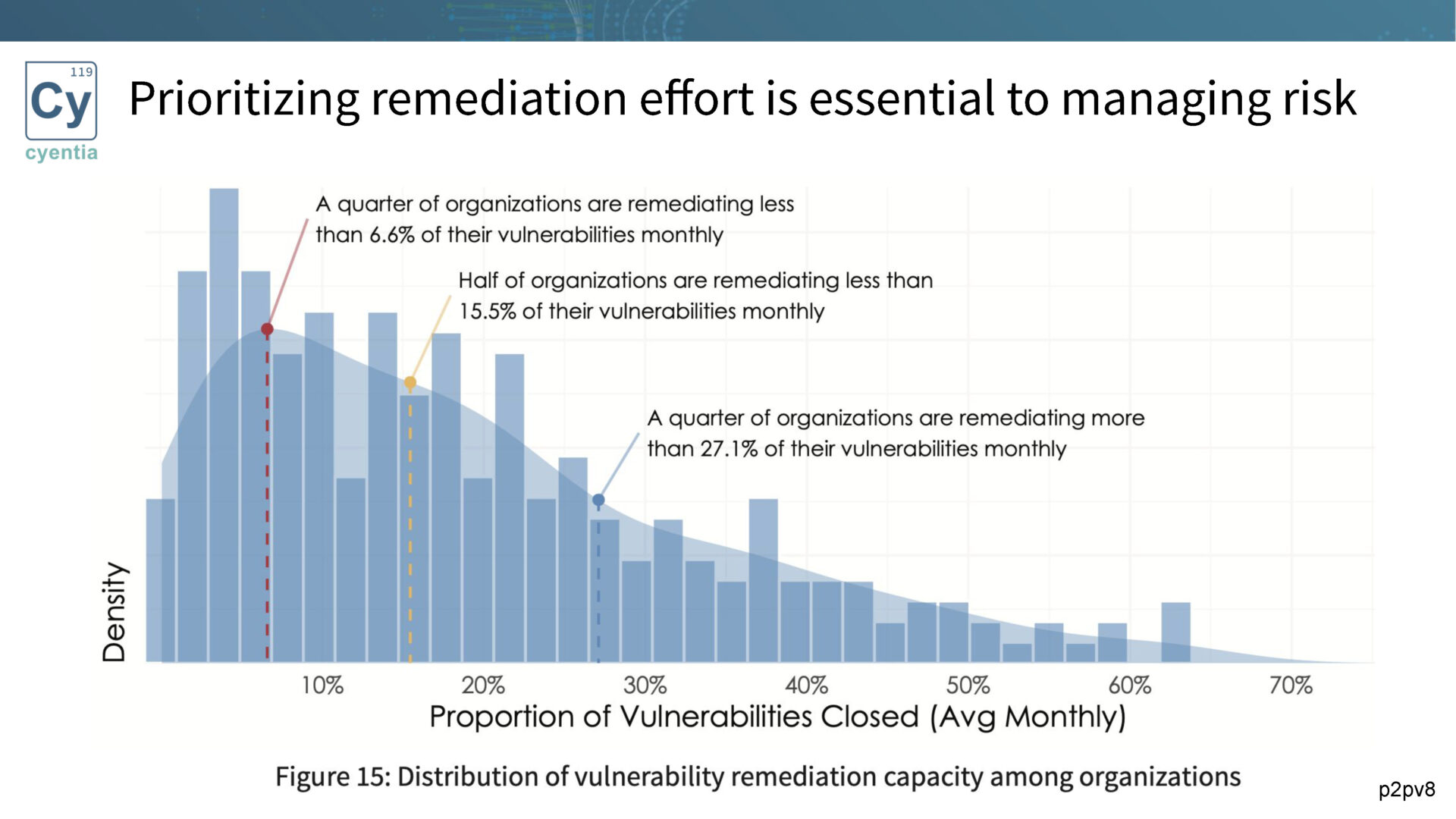
Exploitation as a Prioritization Factor
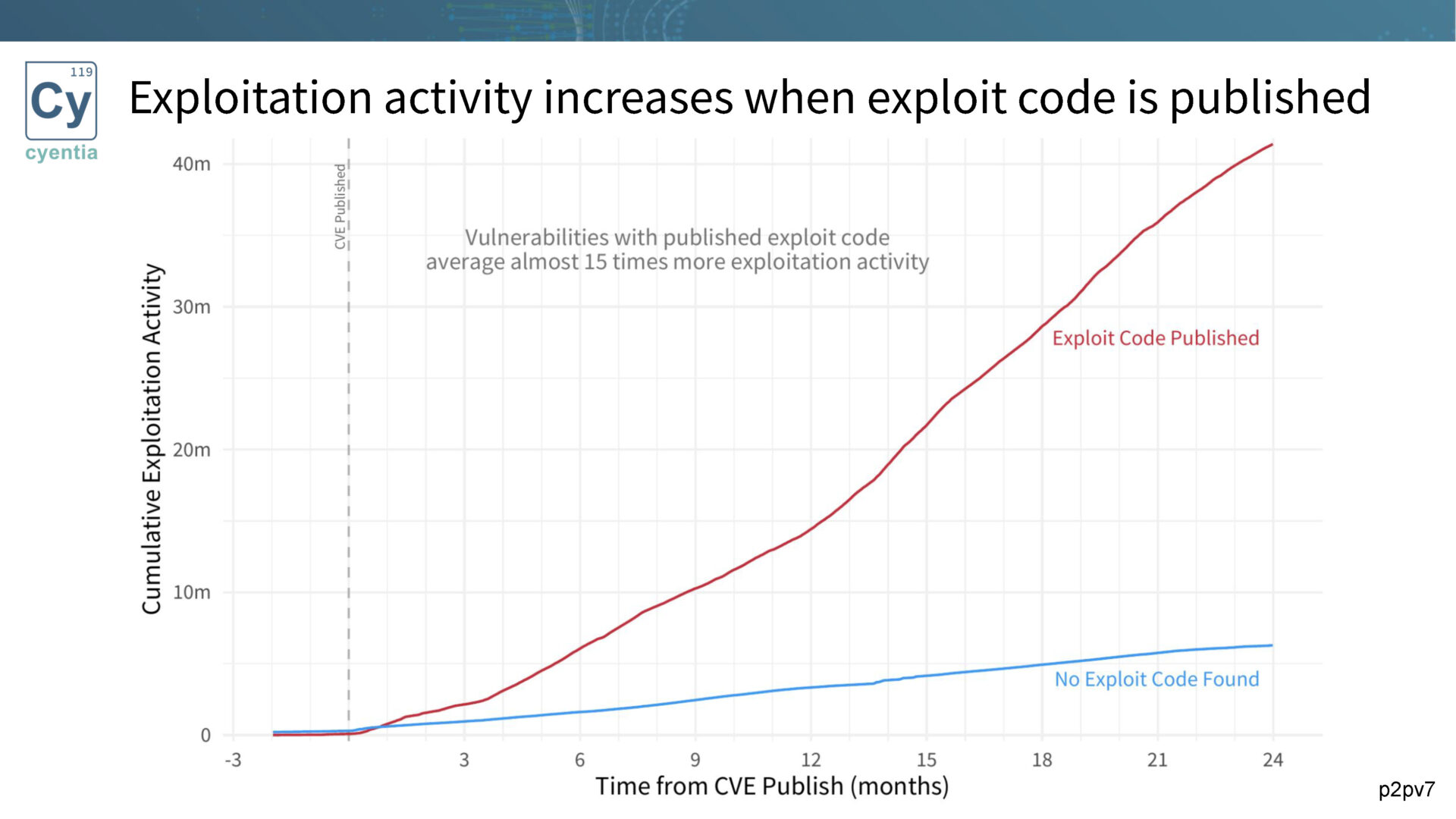
Traditional methods, like CVSS, fall short in effective prioritization. That’s why we advocate for tracking exploitation as a key factor.Research has consistently shown that vulnerabilities with published exploit code are more likely to be exploited. By monitoring exploitation activity and prioritizing based on the presence of exploit code, organizations can focus their efforts on mitigating the most critical threats.
Sources of Exploit Code
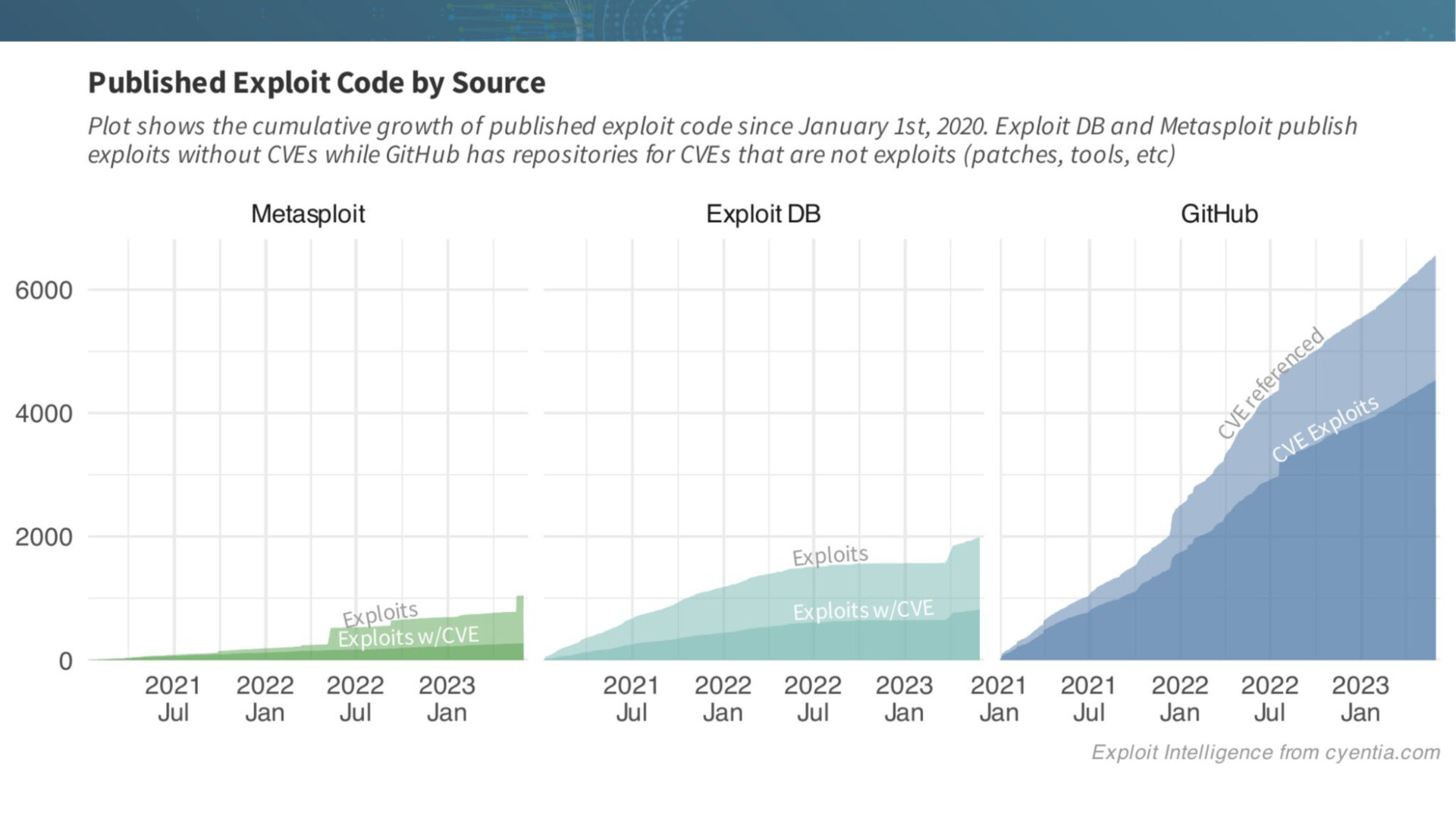
Not all sources of exploit code are created equal. We examine three primary sources: Metasploit, Exploit DB, and GitHub.While each has its strengths and challenges, GitHub has emerged as a popular platform for exploit authors to publish their code. The ease of posting and sharing code on GitHub has contributed to its rapid growth as a reliable source of exploit code.
Visualizing the Overlap
To better understand the relationships between these sources, we visualize the overlap between Metasploit, Exploit DB, and GitHub. The correlation shows that Metasploit and GitHub have significant overlap, while Exploit DB maintains its unique value. 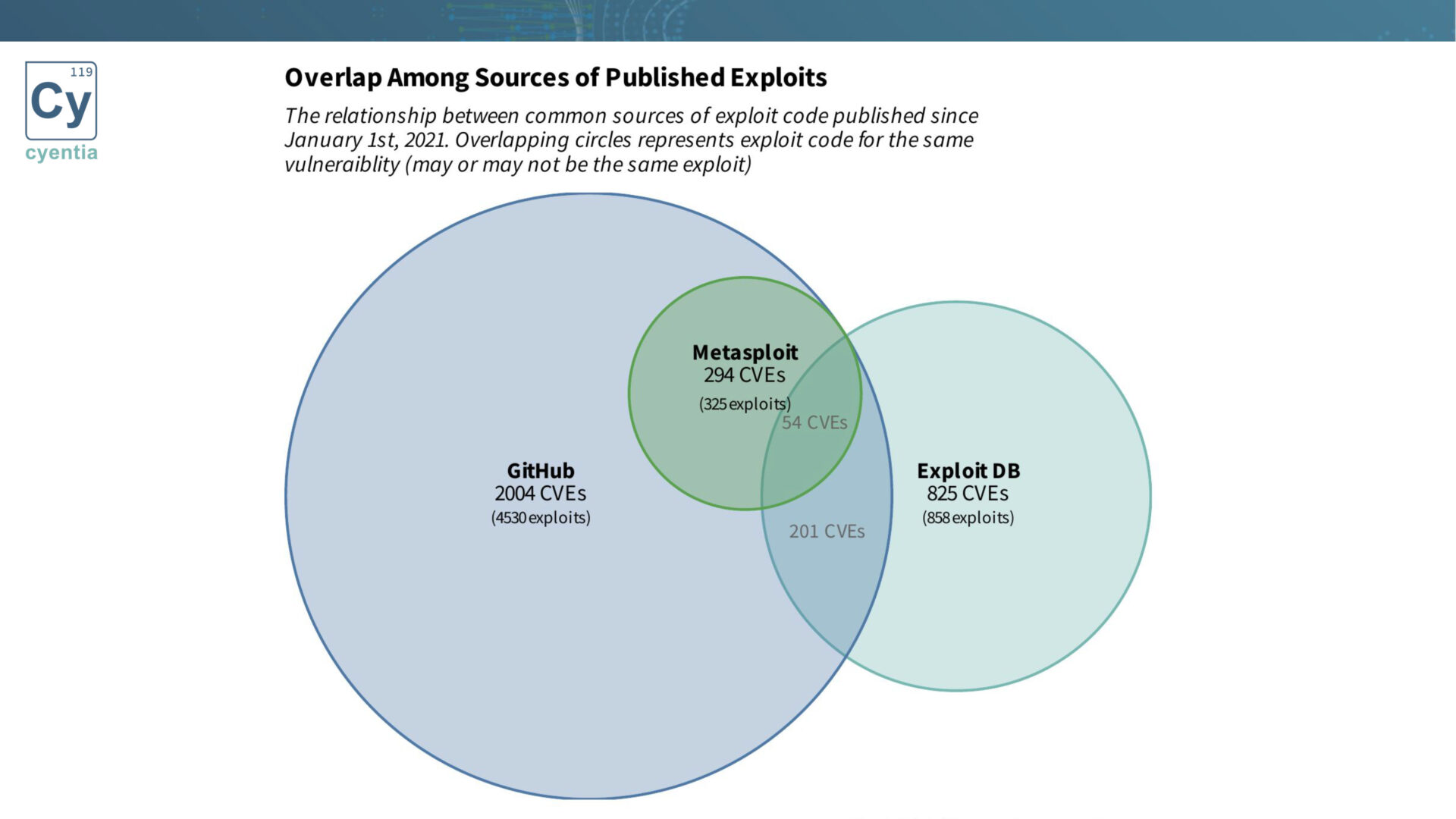
By analyzing these overlaps, organizations gain insights into the availability and prevalence of exploit code across different platforms.
Check out Jay’s article that covers these sources in more detail.
Exploitation Activity Insights
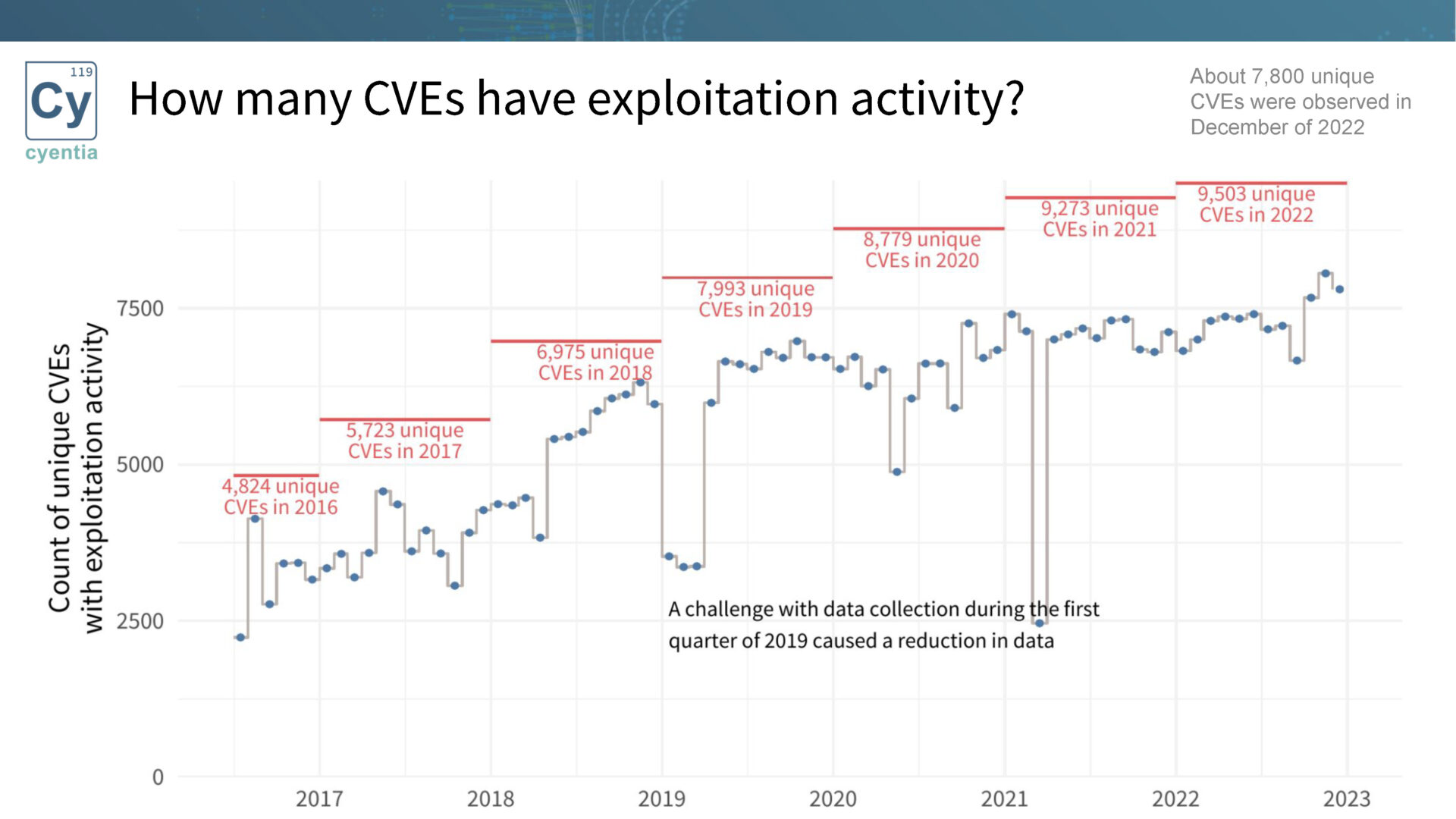
We explore the exploitation activity timeline and its connection to exploit code publication. Research reveals, as noted above, that exploitation activity is significantly higher when exploit code is published.Furthermore, the speed of first exploitation activity is much faster when exploit code exists. By leveraging this information, organizations can proactively remediate vulnerabilities before they are exploited in the wild.
Looking Ahead
Threat-driven remediation based on exploit intelligence offers organizations a proactive approach to vulnerability management. By utilizing signals like exploit code publication and monitoring exploitation activity, it becomes possible to prioritize remediation efforts effectively.
In conclusion, effective vulnerability prioritization is essential in the face of increasing threats. By leveraging exploit intelligence and focusing on the threat side of vulnerability management, organizations can better understand and mitigate their risks. Stay tuned for the second part of this blog post!
Watch the companion recording
“Enhancing Cyber Resilience: Leveraging EIS and Shifting CVEs”
Disclaimer: Please note that the findings presented in this blog post are part of an ongoing research effort and should be interpreted in that context. The insights shared here are subject to further validation and refinement as our exploration progresses.
We invite you to join the conversation and share your thoughts and questions on this topic.
Together, we can advance our understanding of vulnerability management and strengthen our collective defenses against emerging threats.
 Want an even more one-on-one opportunity to ask your questions? Schedule your meeting with Jay Jacobs at Black Hat in Las Vegas August 9th & 10th!
Want an even more one-on-one opportunity to ask your questions? Schedule your meeting with Jay Jacobs at Black Hat in Las Vegas August 9th & 10th!
Spots are limited, reserve your time now!

Leave a Reply
Want to join the discussion?Feel free to contribute!