In our previous blog post, we discussed the importance of prioritizing vulnerability remediation based on exploit intelligence. But once vulnerabilities are prioritized, the question arises: How fast should they be fixed? In this follow-up post, we delve deeper into the concept of timing remediation efforts and explore the dynamics of exploitation activity. Our ongoing exploration aims to provide insights into setting informed, threat-driven deadlines for vulnerability remediation.
The Timing Conundrum
While it’s clear that high-risk vulnerabilities should be addressed promptly, determining the optimal speed for remediation is more nuanced. The answer lies in understanding the spread of exploitation activity and how it varies across organizations and vulnerability types. By examining the timelines and rates of exploitation, we gain valuable insights into the urgency of remediation efforts.
Exploring the Exploitation Timeline
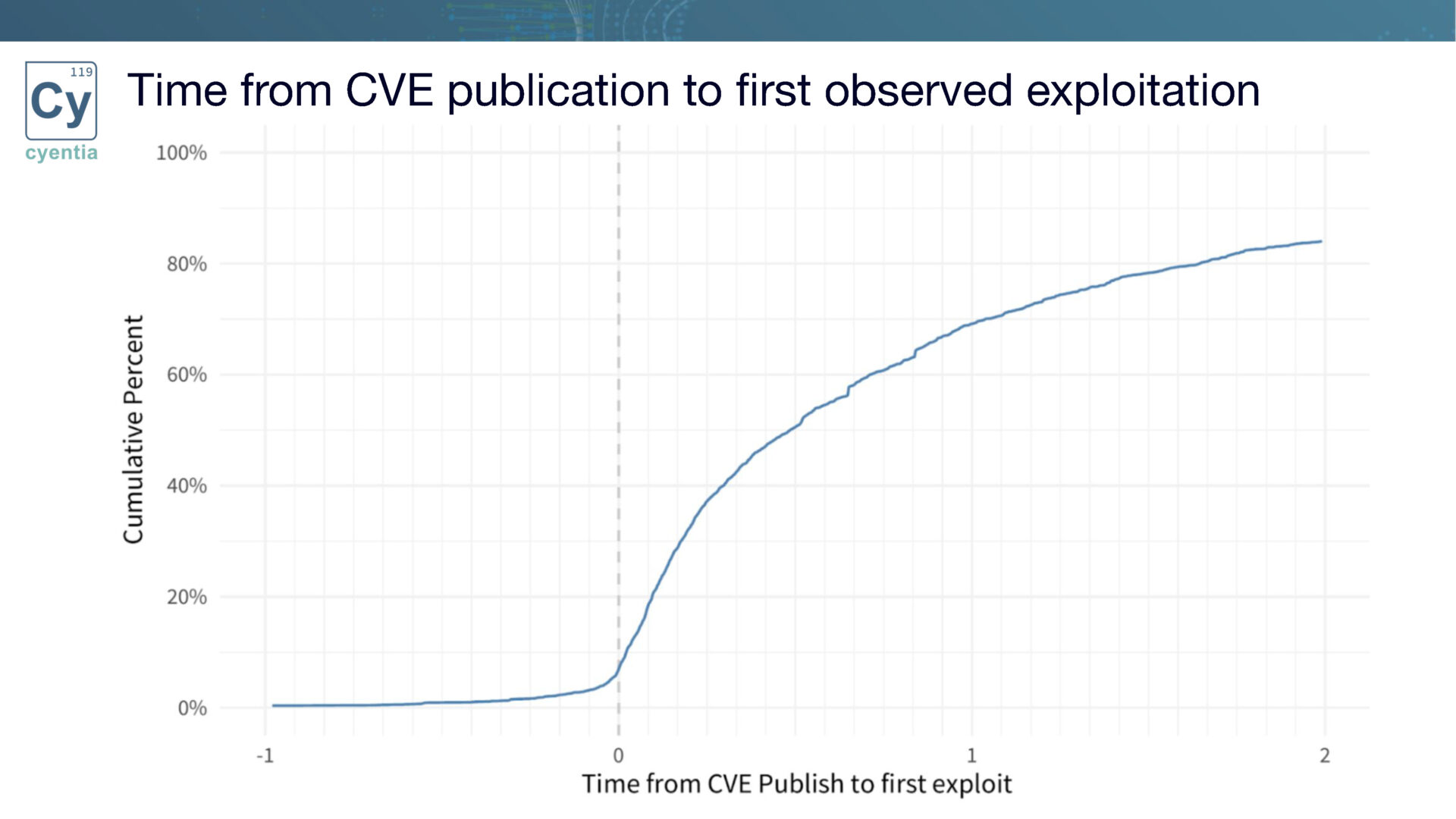
Our research reveals that exploitation activity does not occur immediately after a vulnerability is published. Instead, there is often a delay before organizations detect and address the vulnerability. This delay offers organizations an opportunity to act proactively and stay ahead of the exploitation curve. By understanding the timeline of exploitation, organizations can gauge the urgency of remediation based on their position within the target population.
Differentiating Targeted Organizations
Organizations vary in terms of their exposure to exploitation attempts.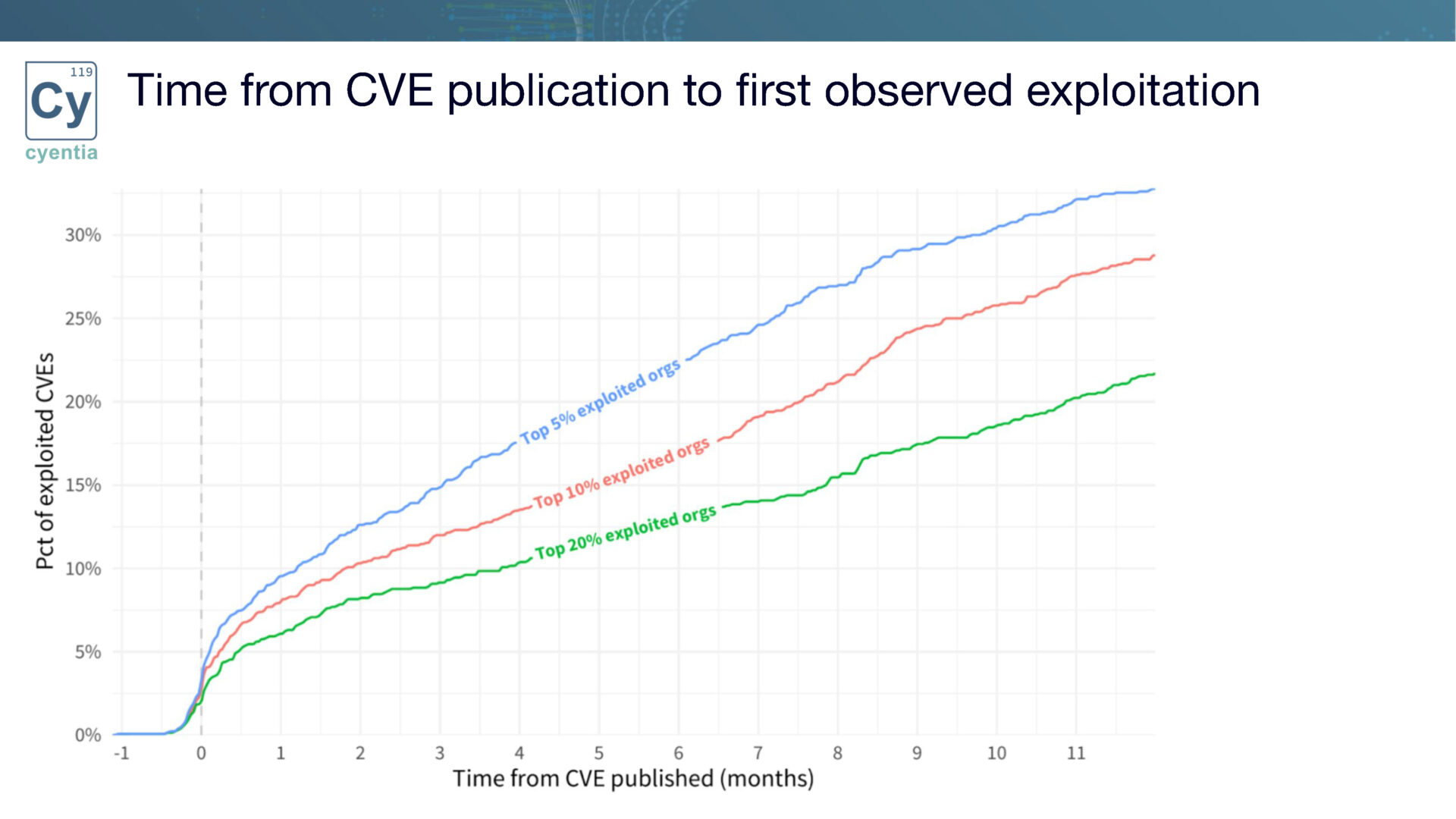 We categorize organizations into different tiers based on their likelihood of being targeted. For example, the top 5% of organizations experience the highest exploitation activity, while the top 20% face a slightly lower level. By analyzing the vulnerability landscape from this perspective, organizations can better gauge the speed at which they need to work to mitigate risks effectively.
We categorize organizations into different tiers based on their likelihood of being targeted. For example, the top 5% of organizations experience the highest exploitation activity, while the top 20% face a slightly lower level. By analyzing the vulnerability landscape from this perspective, organizations can better gauge the speed at which they need to work to mitigate risks effectively.
Balancing Risk and Remediation
To illustrate the varying remediation workload for organizations at different positions within the target population, we present a visualization of the overall number of exploited vulnerabilities.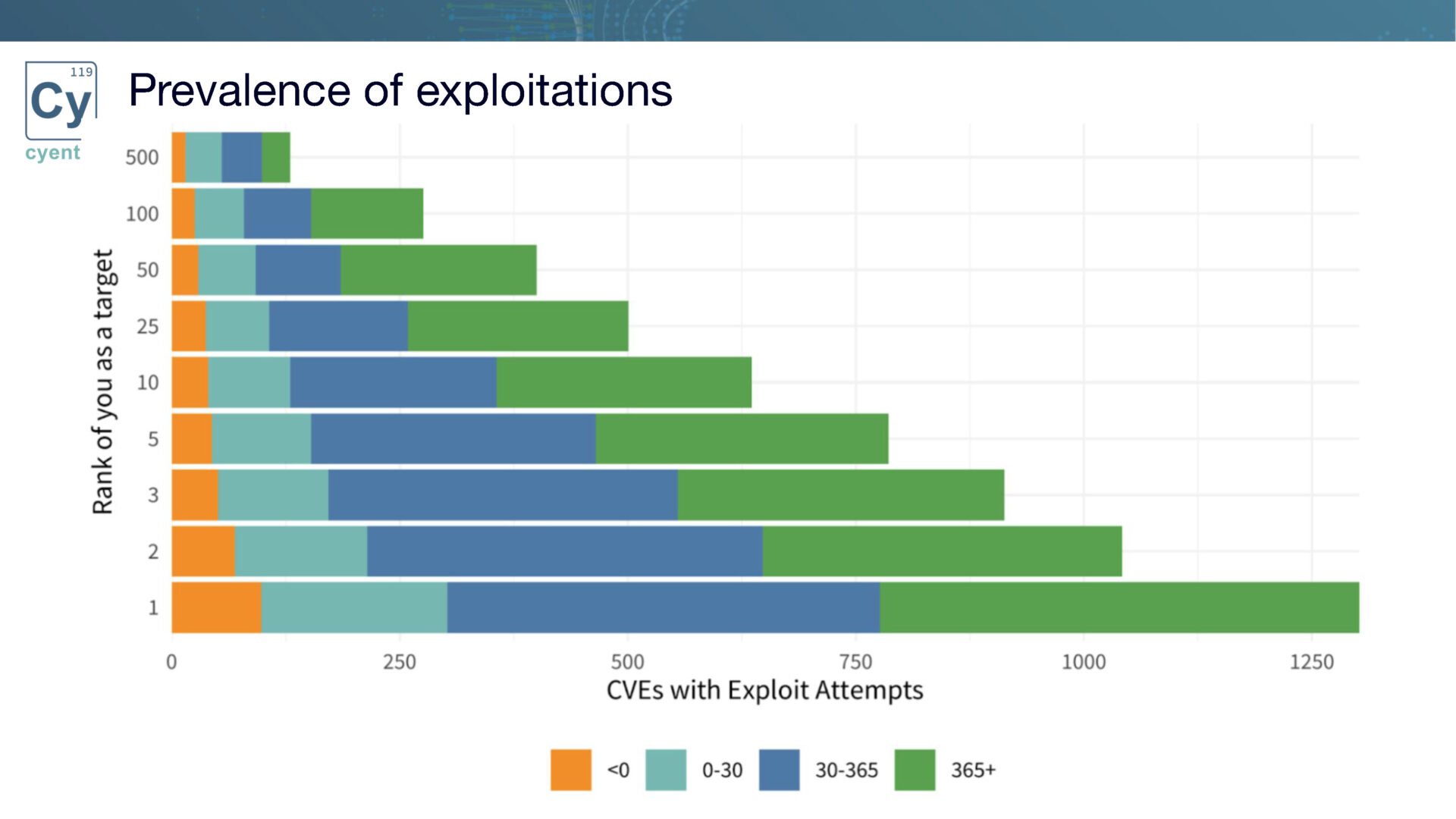 This chart provides insights into the number of vulnerabilities an organization would need to address based on its position in the target chain. For instance, the bottom position represents the scenario where an organization is the primary target for every single CVE, being the first organization targeted for exploitation attempts. Understanding this breakdown enables organizations to prioritize their remediation efforts based on the volume and urgency of vulnerabilities they face.
This chart provides insights into the number of vulnerabilities an organization would need to address based on its position in the target chain. For instance, the bottom position represents the scenario where an organization is the primary target for every single CVE, being the first organization targeted for exploitation attempts. Understanding this breakdown enables organizations to prioritize their remediation efforts based on the volume and urgency of vulnerabilities they face.
The Path Forward
While our exploration is still ongoing, we are committed to uncovering insights that can enhance vulnerability management practices. Our research seeks to bridge the gap between vulnerability prioritization and timely remediation, empowering organizations to make informed decisions regarding their cybersecurity defenses. By combining exploit intelligence with a thorough understanding of exploitation timelines, organizations can optimize their remediation strategies.
The question of how fast vulnerabilities should be remediated remains a critical concern for organizations. By examining the dynamics of exploitation activity and understanding the spread of vulnerabilities across different tiers of organizations, we can establish more accurate timelines for remediation efforts. Our ongoing exploration aims to equip organizations with the knowledge and insights needed to enhance their threat-driven remediation strategies. Stay tuned for further updates as we delve deeper into this important topic.
Watch the companion recording
“Enhancing Cyber Resilience: Leveraging EIS and Shifting CVEs”
Disclaimer: Please note that the findings presented in this blog post are part of an ongoing research effort and should be interpreted in that context. The insights shared here are subject to further validation and refinement as our exploration progresses.
We invite you to join the conversation and share your thoughts and questions on this topic.
Together, we can advance our understanding of vulnerability management and strengthen our collective defenses against emerging threats.
 Want an even more one-on-one opportunity to ask your questions? Schedule your meeting with Jay Jacobs at Black Hat in Las Vegas August 9th & 10th!
Want an even more one-on-one opportunity to ask your questions? Schedule your meeting with Jay Jacobs at Black Hat in Las Vegas August 9th & 10th!
Spots are limited, reserve your time now!



Leave a Reply
Want to join the discussion?Feel free to contribute!