/wp-content/uploads/2023/06/PPhreaksSmall.jpg
900
1600
Ben Edwards
/wp-content/uploads/[email protected]
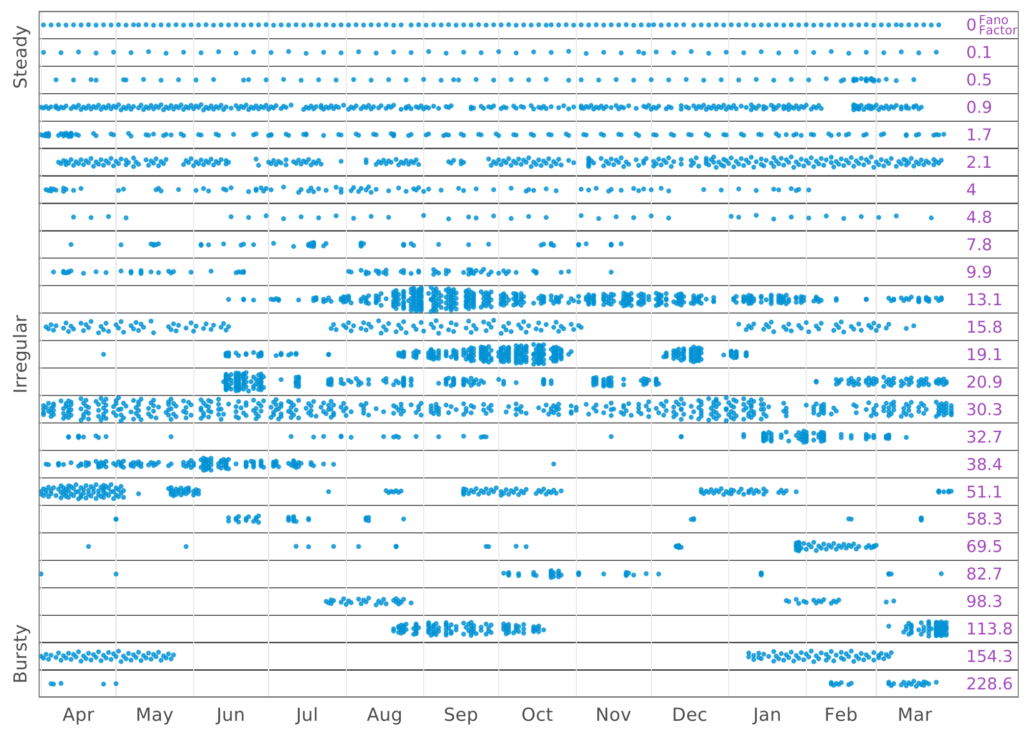
Ben Edwards2023-06-02 12:15:322023-06-05 12:15:05¾ of Century of Cybersecurity Solitude
/wp-content/uploads/fig03-1.png
1167
2100
Ben Edwards
/wp-content/uploads/[email protected]
Ben Edwards2022-03-22 16:36:552022-03-22 16:37:48Don't fear the smoother
/wp-content/uploads/bump_difficulty.png
1500
2100
Ben Edwards
/wp-content/uploads/[email protected]
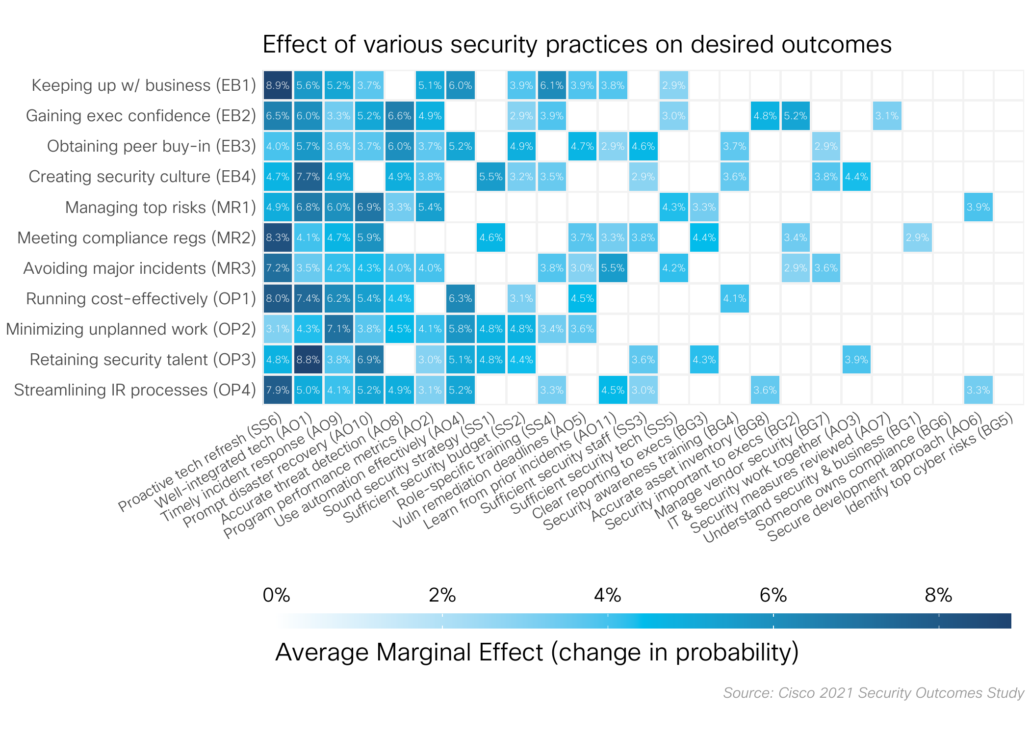
Ben Edwards2022-01-03 13:51:232022-01-20 21:51:23Cisco Security Outcomes Study Methodology Post II: The Rise of Item Response Theory
/wp-content/uploads/fig16.png
1500
2100
Ben Edwards
/wp-content/uploads/[email protected]
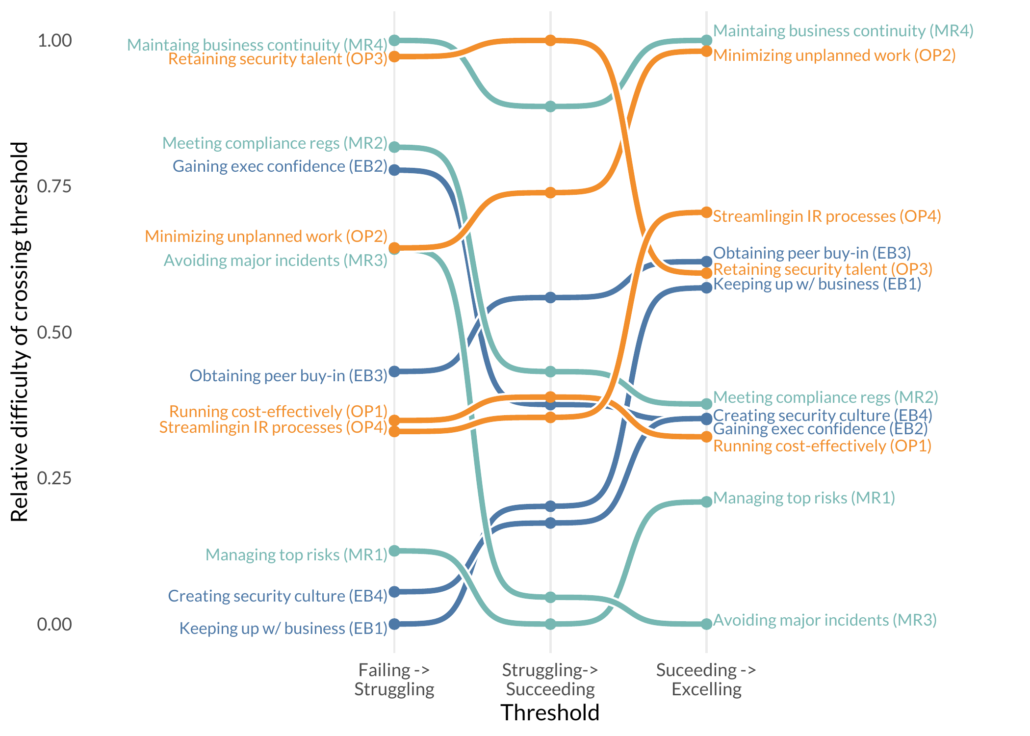
Ben Edwards2021-11-30 17:46:032022-06-14 12:46:01Cisco Security Outcomes Study methodology post! Attention Stats Nerds!
/wp-content/uploads/fig11_annotated.png
1500
2100
Ben Edwards
/wp-content/uploads/[email protected]
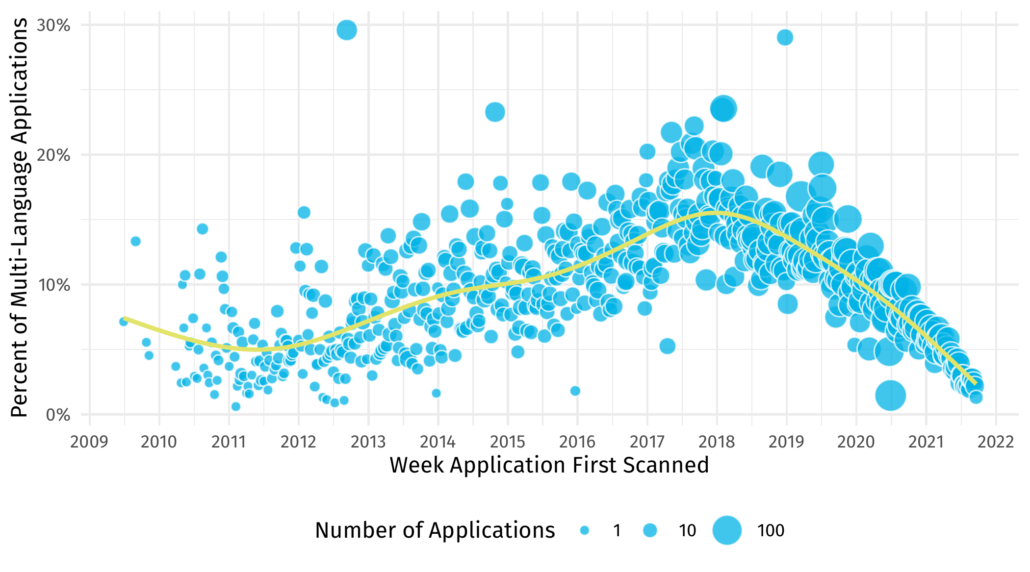
Ben Edwards2019-11-12 13:00:012021-07-29 19:20:43Application Security and Burstiness
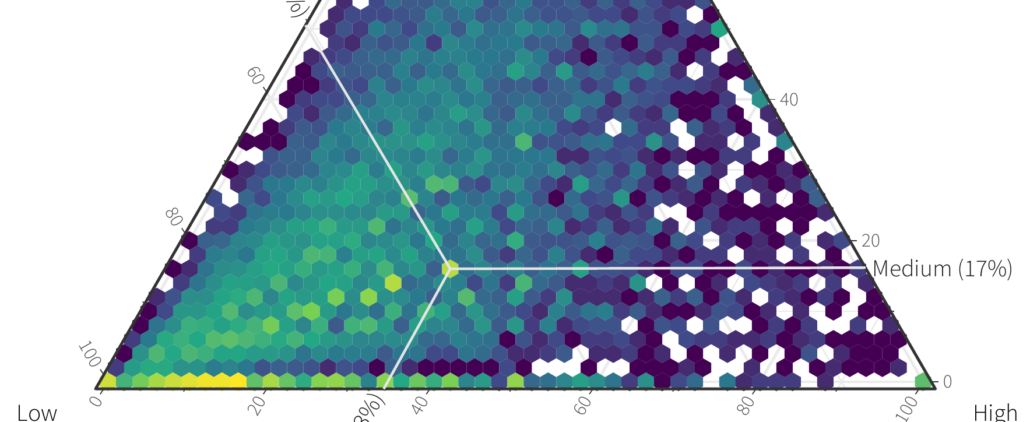
/wp-content/uploads/Fig7-e1556729294336.png
724
1767
Ben Edwards
/wp-content/uploads/[email protected]
Ben Edwards2019-04-19 16:57:312019-05-16 10:34:07Ternary plots for visualizing (some types of) 3D data
/wp-content/uploads/DSC01605-e1556729201681.jpg
686
1920
Ben Edwards
/wp-content/uploads/[email protected]
Ben Edwards2019-04-19 16:53:212019-05-29 13:19:42Introducing Cyentia's new data scientist
© Copyright 2024 Cyentia Institute
Scroll to top