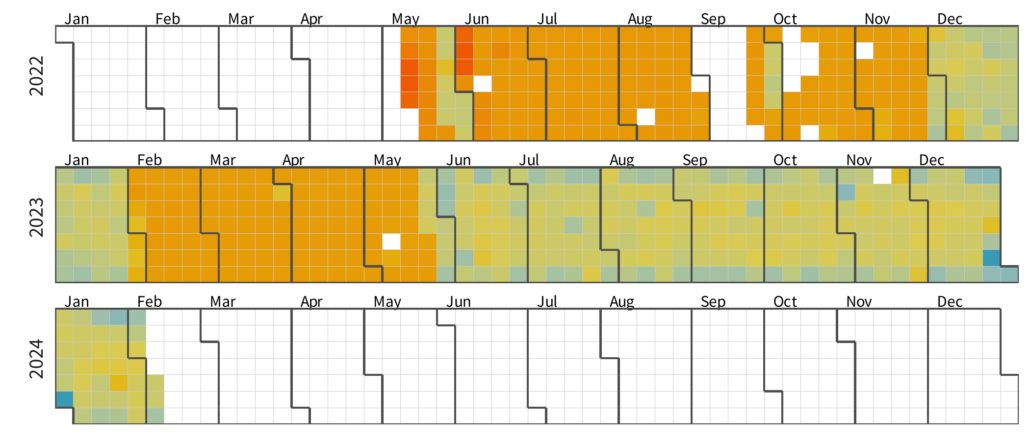
/wp-content/uploads/2024/03/calendar-forblog.png
900
2100
Jay Jacobs
/wp-content/uploads/[email protected]
Jay Jacobs2024-03-15 13:13:072024-03-15 23:25:08Call for Sponsors: Inaugural Exploit Prediction Annual Report
/wp-content/uploads/gremlin-feature.jpg
302
705
Stephanie
/wp-content/uploads/[email protected]
Stephanie2021-12-23 11:01:472022-06-14 12:37:21Looking Back on 2021
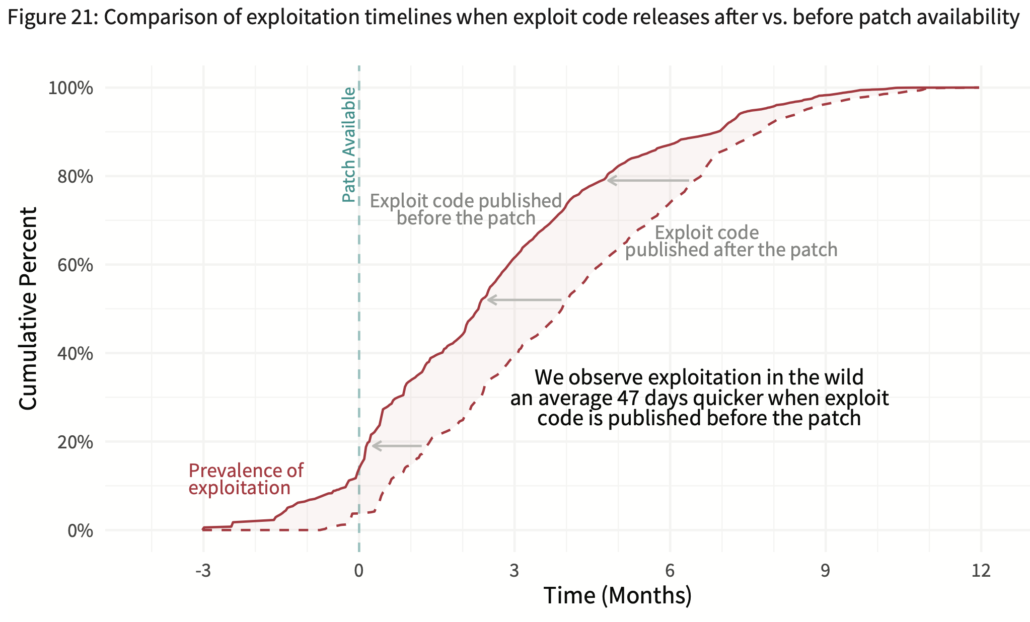
/wp-content/uploads/p2pv6fig21.png
1236
2046
Wade Baker
/wp-content/uploads/[email protected]
Wade Baker2021-01-21 08:00:222022-06-14 16:05:36I Once Called Vuln Researchers NVPs; Are They MVPs Instead?
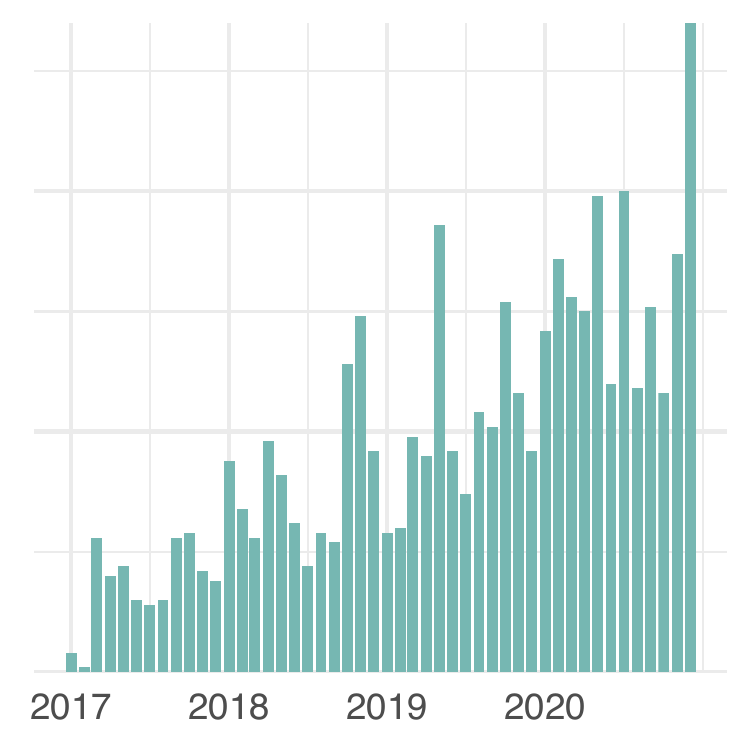
/wp-content/uploads/rawcount_by_date_github.png
750
750
Jay Jacobs
/wp-content/uploads/[email protected]
Jay Jacobs2021-01-06 13:52:432022-06-14 16:10:00GitHub: A Source for Exploits
/wp-content/uploads/P2P_vol3_web.png
385
634
Wade Baker
/wp-content/uploads/[email protected]
Wade Baker2019-03-12 08:55:532019-03-12 09:34:26Prioritization to Prediction, Vol 3: Wade’s Take
© Copyright 2024 Cyentia Institute
Scroll to top