The Cyentia Institute is seeking multiple sponsors to support R&D efforts leading to the publication of a meta-study of MITRE ATT&CK tactics and techniques. Details on this call are provided below. If interested, please reach out to [email protected].
What’s the goal of the study?
More and more cybersecurity industry reports include statistics around commonly detected ATT&CK techniques. That’s great in terms of having more data available for defenders and decision-makers, but a challenge arises to draw collective conclusions from them regarding the most common techniques. Cloud, network, and endpoint vendors/products have different vantage points, varying levels of visibility across tactics, and thus tend to report vastly different techniques. Incident responders have a different perspective than intelligence analysts. Reports from law enforcement agencies will differ from those of law firms. And the list goes on.
This study will compare and contrast all those sources to find common threads among them that will aid organizations seeking to build a more threat-informed defense.
How will the study be conducted?
We’re proposing to undertake several tasks in conducting this research:
- Identify published industry reports that include statistics on ATT&CK techniques
- Categorize sources based on data collection methodology (i.e., endpoint detection vs IR service)
- Compare and contrast stats on ATT&CK techniques reported by all sources
- Determine the most common ATT&CK techniques overall and for each data collection method
- Prioritize mitigation strategies based on relevancy to common ATT&CK techniques
- Prepare an publish an analytical report detailing the findings of this research
If we receive sufficient additional sponsorship funding, we’d also like to make one or more of the following enhancements to the Cyentia Cybersecurity Research Library (a freely-searchable compendium of thousands of published industry reports):
- An ATT&CK-based search engine that allows users to find reports that mention specific tactics or techniques and where those mentions are located in the report
- A series of regularly updated (and potentially interactive) charts on the Library website that tracks trends around common tactics and techniques over time
- Develop a model that incorporates natural language processing (NLP) that recognizes text describing an ATT&CK technique that doesn’t explicitly reference the technique ID or name (i.e., “attackers used stolen passwords to access..” would be classified as T1078 – Valid Accounts)
Why should the Cyentia Institute do this research?
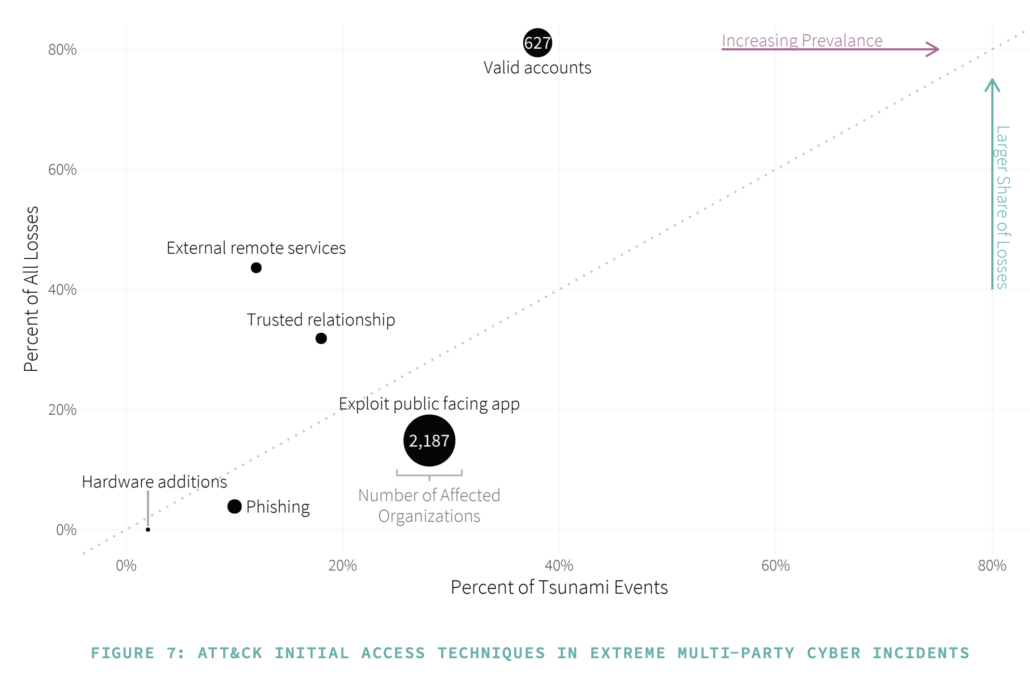
Valid question and thanks for asking it. The Cyentia Institute is a trusted entity with a long track record of conducting high-integrity, data-driven research. One of our founders started Verizon’s Data Breach Investigations Report (itself a multi-source analysis of data from many organizations) and led that team for almost a decade. Cyentia institute has conducted other meta-studies on cyber threats such as our blog series on Measuring Ransomware Prevalence and The State of The State of Application Exploits in Security Incidents. We also regularly incorporate MITRE ATT&CK into our research, as seen in the figure below from the “Tsunami” edition of the Information Risk Insights Report (IRIS). Bottom line: We know how to do this kind of research on exactly this topic (which is why we’ve proposed it).
How much does it cost to be a sponsor?
We’re seeking a flat sponsorship of $25k from all sponsors that we will use to fund tasks 1 through 6 under the prior question/section (all R&D to produce a published study). However, organizations will also be able to increase that amount to sponsor one or more of the enhancements listed above to the Cybersecurity Research Library. Each of those tasks will be scoped based on input from the sponsor and a reasonable cost will be agreed upon to fund the project.
What are the benefits of being a sponsor?
The most important benefit is the satisfaction that you are directly contributing to raising the bar of knowledge and practice in cybersecurity. Plus, you get to work with the incredible Cyentia team! What more could you ask?
Ok, ok…there’s more. We also hope the research will earn the appreciation of the organizations that benefit from it and those sentiments will transfer favorably over to the sponsors who made it possible. Beyond those altruistic and indirect benefits, here’s what sponsors will receive by being involved in this research:
- Recognition in the published report (prominent placement of logo, short description, etc.)
- Recognition in promotional activities related to the report (verbally mentioned in presentations, social tagging, etc)
- Dedicated space (1 page) in the published study to add your perspective and recommendations on the findings
- Media assets that include high-resolution versions of all data visualizations to use in your own promotional activities
- Ability to create a branded version of the study to distribute independently via your own channels (cannot alter main content)
Sponsors of the optional Cybersecurity Research Library enhancements will receive additional recognition specific to those projects (to be discussed/determined as part of scoping).
How can I become a sponsor?
It’s super simple. Just send an email to [email protected] and we’ll follow up to discuss the particulars. Thanks for your interest in enabling a community-oriented approach to cyber defense through making sense of our collective knowledge output.



Leave a Reply
Want to join the discussion?Feel free to contribute!