While working on volume 2 of the Investigative Cybercrime Series, Reining In Ransomware, we were curious about the functionality of the most common ransomware strains. The thinking went like this: if we can identify what they do, then we can use the frequency info from actual cases to weight those actions and find key protections that have the most coverage for ransomware. This naturally led us to investigate whether MITRE’s ATT&CK framework could be of use. Not only were we able to enumerate the strains’ functionality (techniques, in threat intel/ATT&CK parlance), but—bonus points—they included mappings from techniques to defenses (aka mitigations).
You can find some of this analysis broken up by tactics—albeit coarsely—in the report. Those results are most compelling from the perspective of someone looking to beat ransomware at multiple points along the killchain (which is a really good idea; you should totally do that!) But as a recovering risk manager, I saw an opportunity to answer a slightly different question: could we quantify the overall benefit of a given control based on mappings to multiple techniques, informed by strains’ frequency?
If you’re thinking, “um, ok, but who cares?”, I’d like to congratulate you on your charmed professional life and bid you good day! However, I recall being asked on multiple occasions—after having made my case to prioritize a particular risk scenario and select one or more protections based on feasibility, opportunity, cost, etc.—whether there were other collateral benefits of implementing the recommended control(s). I’ll confess, I always found answers to this question a bit…hand-wavy. But while playing with different ways to present the technique-to-mitigation data, I felt like a sankey/alluvial plot could help us out.
Visualizing “flow”
This figure ties together the top 10 strains in the Arete dataset to their known techniques, and further to the relevant mitigations. There are a few ways to read this and at least one way to not read it—i.e. tracing the tiny spaghettini from Zeppelin through a specific technique, etc. etc.
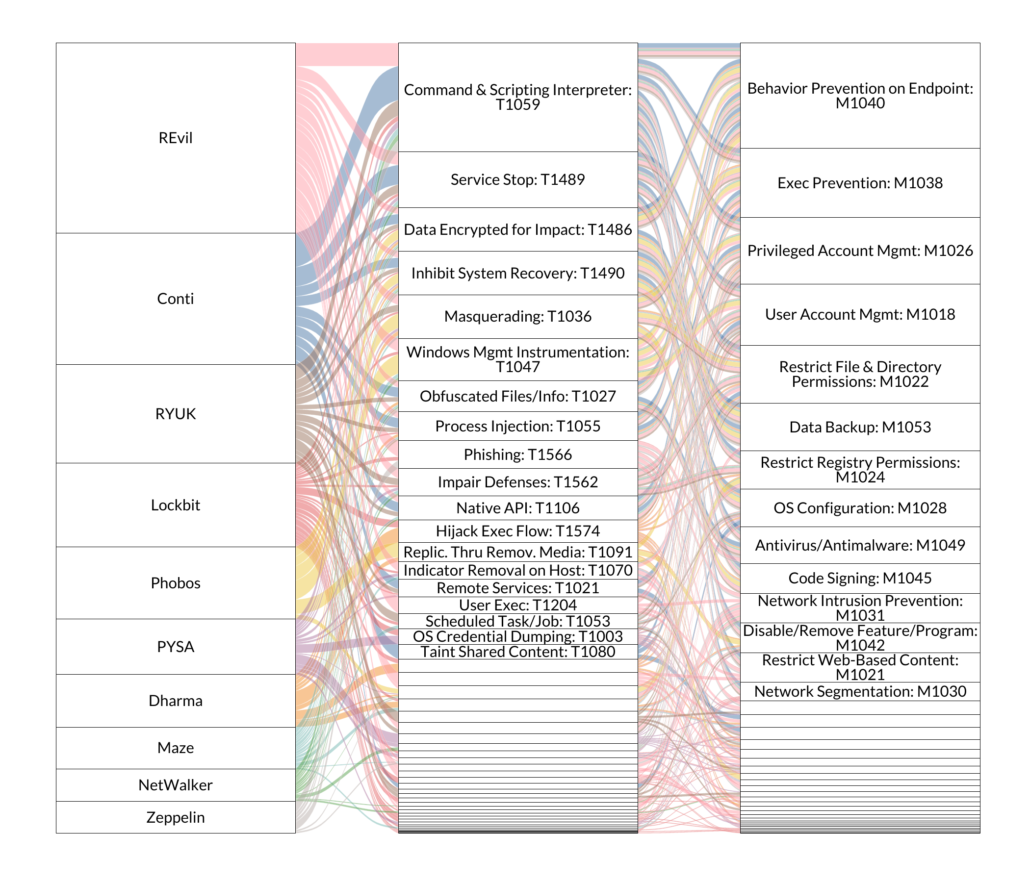
Some things jump out on the left: note how some families rely on relatively few techniques (Phobos – 6) while others use considerably more (Lockbit – 31). Also, note that some techniques link to relatively few families—or sometimes a single strain, as is the case with Conti and Taint Shared Content (T1080). Now, let’s take a moment to understand what the middle column is telling us: after accounting for frequency among the top 10 strains, Command & Scripting Interpreter (T1059) was the most common technique. Seems like a ransomware mitigation strategy should probably include one or more ways to address that, no?
However, for the “bang for buck”-type question posed above, the rightmost column is quite interesting. In terms of dealing with the most functionality, Behavior Prevention on Endpoint (M1040) is a clear winner. A potential benefit of this view is that it strips away so much of the potentially distracting trappings of ransomware—e.g. the monetization strategy, the ethics of paying ransoms, nation-state affiliations, etc. What remains is the somewhat obvious but too often overlooked fact that, at its core, ransomware is… malware. A second observation of the mitigations column is that most of them tie back to several strains, sometimes more than once. This is a little more justification to worry less about specific trending strains when considering protections, at least beyond staying apprised of general shifts in strategy—e.g. increasing rates of double extortion.
Looking for more?
If you’re interested in other insights gained from analyzing nearly 1,500 ransomware cases, I’d encourage you to check out the full report Reining In Ransomware, the second volume of our Investigative Cybercrime Series, in partnership with Arete. And if you haven’t read volume 1, Mitigating Ransomware’s Impact, give it and its accompanying post on Information Asymmetry a read as well. In them, we cover trends in demands and payment, payment rates, effectiveness of MFA and backups, and more!



Leave a Reply
Want to join the discussion?Feel free to contribute!