Our recent report Mitigating Ransomware’s Impact, produced in partnership with Arete, provides a convenient excuse to reflect on ransomware developments in recent years. Old school readers may remember some of our first blog posts (a three-part series, circa July 2017) were about ransomware. In them, Wade and Jay performed some meta-analysis on payment rates, demand amounts, and prevalence. I encourage you to revisit them, as I think they still hold up as a great snapshot from five years ago, setting the stage for appreciating how much has changed since then. And oh, how things have changed…
One big development, in our eyes at least, has been our own research in this space. We first looked into ransomware’s prevalence in IRIS Xtreme and continued in IRIS Tsunami. We currently provide this information at an industry level via IRIS Retina, and plan to include it in IRIS 2022. And in Mitigating Ransomware’s Impact, we’ve now explored payment rates, demand amounts, and payment amounts.
As with any new research project, this one brought opportunities to learn way more about the topic–even one as seemingly well-worn as ransomware. I personally found the most fascinating element to be the number and variety of non-technical considerations. The report covers a handful of them, mostly related to negotiation tactics familiar to anyone who has ever shopped for a used car: sticker shock, low-balling, sunk cost, time-pressure, etc. I’d like to share two big issues that came up during production: 1) should victims pay at all? and 2) does sharing payment information help criminals?
Should victims pay at all?
This question is interesting on its own merit, but it was pertinent to us because of its implied corollary: if victims shouldn’t pay, would we be complicit in reinforcing bad norms of behavior by publishing a report about ransom payments? The topic became even more timely when, right before release, North Carolina enacted a law prohibiting state agencies and local governments from paying ransoms or communicating with entities attempting to extort them (section 38.13 of SL2021-180). TL;DR: some victims have paid and will continue to pay, and we think that by handling the subject carefully we can inform defenders in a way that ultimately hurts attackers’ bottom lines.
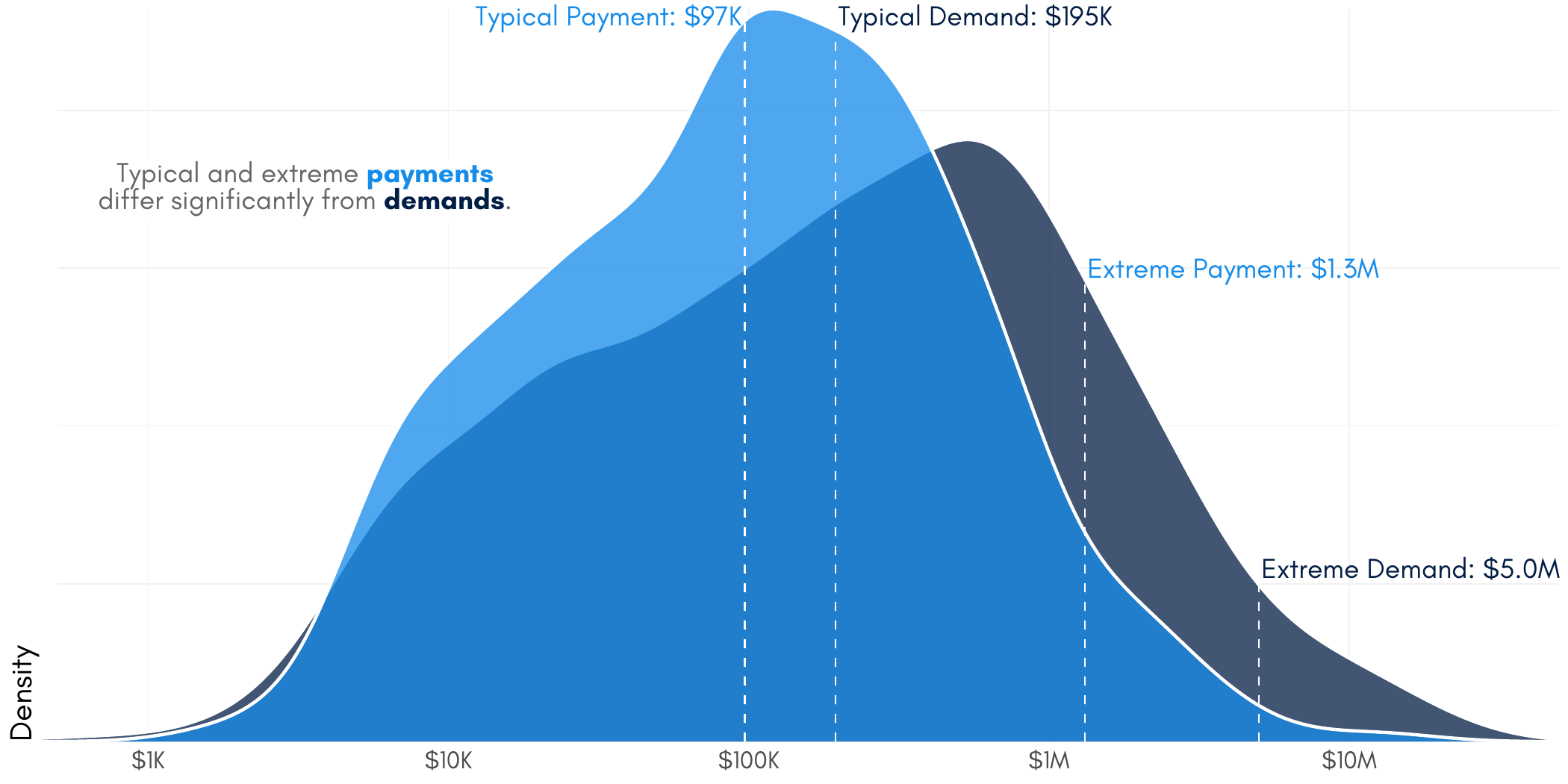
Figure 4 – Ransom demands vs. payments
There are some compelling reasons to drive down ransomware gangs’ profits. One terrific resource we came across is Combating Ransomware, released by the Institute for Security and Technology’s Ransomware Task Force (RTF) in 2021. From its section dedicated to the topic of prohibiting ransomware payments:
The argument in favor of a ransom ban holds that ransomware is primarily motivated by profit, and if the potential for a payout is removed, attackers will shift away from this tactic. A further argument is that ransom profits are used to fund other, more pernicious crime, such as human trafficking, child exploitation, terrorism, and creation of weapons of mass destruction.
Pretty cut and dry then: you’re either in favor of [insert terrible criminal activity] or against it, right? Whoa there, cowpoke; there’s more to the story. Even the fine folks on the RTF didn’t reach consensus on the topic. And before you write that off as “consensus is hard,” bear in mind that they did manage to produce a framework of 48 specific actions, prioritized and organized, describing a systemic, global approach to mitigating the ransomware problem. (You can learn more about progress made in the last year by watching the RTF’s A Year of Action event from May 2022.)
As with so many policies–cyber and otherwise–it turns out that signaling that you’re “anti bad things” is the easy part; the real work is in practical implementation that actually supports your goal. The RTF identified three key factors to consider before prohibiting payments, without which such policies could be considered ways to “stab the victim”:
- Timeline, including milestones or conditions prior to going into effect.
- Phasing, allowing for incremental change and adaptation.
- Victim protection and support to help offset potential burden on those affected.
So until other measures are implemented to disrupt criminal business operations, it’s probably best not to offload the entire weight of enforcement on the victims. For now, paying a ransom should be considered the last option, but an option nonetheless.
Does sharing payment information help criminals?
Another question that came up was whether publishing information about payment rates and amounts would help criminals. Put another way, would this equip ransomware gangs to coordinate on pricing, ultimately hurting victims even more? I’d like to tweak the question a bit: does publishing such information help criminals more than it helps potential victims?
It’s generally accepted that price transparency helps consumers, and as loathe as I am to make the comparison, extortion operates as a perverse form of market. Some recent research has called into question the conventional wisdom of price transparency’s unalloyed positivity. In Who Benefits from Information Disclosure? The Case of Retail Gasoline. (American Economic Journal: Microeconomics, 11 (2)), author Fernando Luco explores the effect of an online price-disclosure policy in the Chilean retail-gasoline industry. From the conclusions section:
Price-disclosure policies can have pro- or anti-competitive effects depending on whether consumer search—the demand-side response to disclosure—or price coordination—the supply-side response—dominates.
Applied in this context, it comes down to who makes better use of the information. We’re fairly confident that the typical ransomware gang already has access to considerably more payment information compared to the typical victim, so all that’s left is to share it with as many defenders as possible!
It’s also worth noting that we’re not the first to share information about ransom payment rates and amounts, but we might be among the few to do so responsibly. For example, both demands and payments are distributed log-normally, so we should take particular care when selecting our measure of central tendency to describe “typical.” This is especially important when such numbers–e.g. the average–have the potential to price anchor negotiations in the attacker’s favor by being overly influenced by rare, extreme values. In this case, the average payment is 3.5x the typical payment (calculated as the geometric mean).

Table 1 – Important values for ransom demands and payments
We understand that citing BIG SCARY NUMBERS is usually a way of trying to bring attention to a serious issue in hopes of motivating action. But it’s important to consider possible unintended consequences. Returning to the marketplace comparison, this is similar to how one’s belief in inflation trends can result in behavior that facilitates inflation. Therefore, believing that payments are on the rise may actually cause payments to rise. In this case, that would be a shame since our data shows relatively stable–possibly declining–payment amounts across 2020 and 2021.
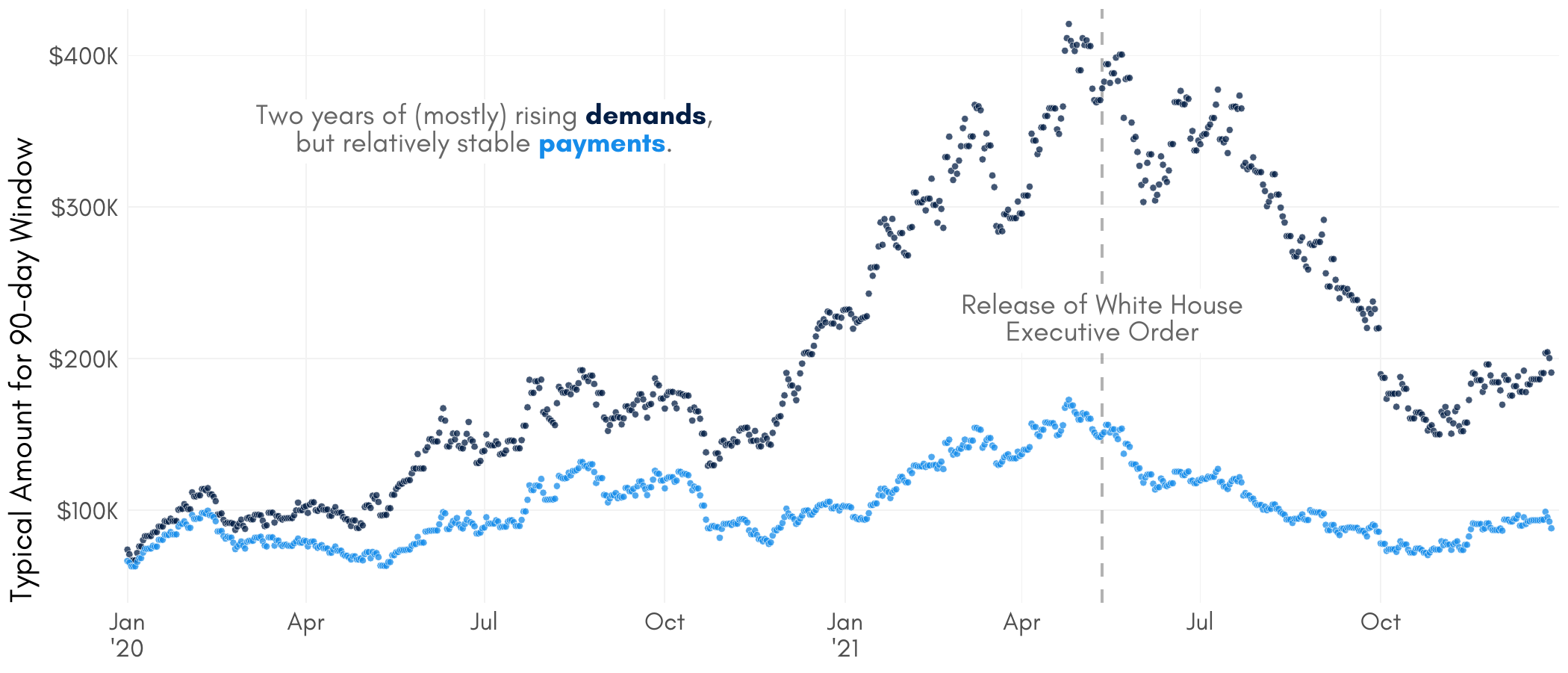
Figure 5 – Demands and payments over time
Cool; so how might this research help?
Shedding light on common negotiation tactics can reduce their manipulative effect. A better understanding of “true” payment norms and payment alternatives can reduce harm to victims and profits to criminals. And evidence about measures taken beforehand which can reduce impact–even when prevention fails–can help defenders prioritize.
It’s no coincidence that we named the report the way we did. Mitigating ransomware’s impact is both the subject and goal of the first volume of our Investigative Cybercrime Series. We’re enormously proud of it, and we hope you’ll give it a read!





Leave a Reply
Want to join the discussion?Feel free to contribute!