One common question I get for EPSS is, “Why does EPSS score CVEs low that are on the CISA KEV List?”
The short answer is that the CISA Known Exploited Vulnerability List (KEV) (I think) relies on manual curation/vetting at a single point in time while EPSS is 100% data driven with a strong, on-going focus on the timing of events. It’d be amazing if they aligned all the time, but we shouldn’t be surprised when they don’t.
Because EPSS is driven by the data and has a strong temporal aspect, it only learns from the exploitation activity it sees (from data partners) and predicts on the vulnerability attributes presented. Those with low EPSS scores on the KEV are more likely to be “Access Vector:Local”, “Confidentiality:None”, require some privileges and/or be without published exploit code. Those with higher EPSS scores tend to have exploit code published, be integrated into pen testing tools and scanners, and/or involve remote command execution/injection.
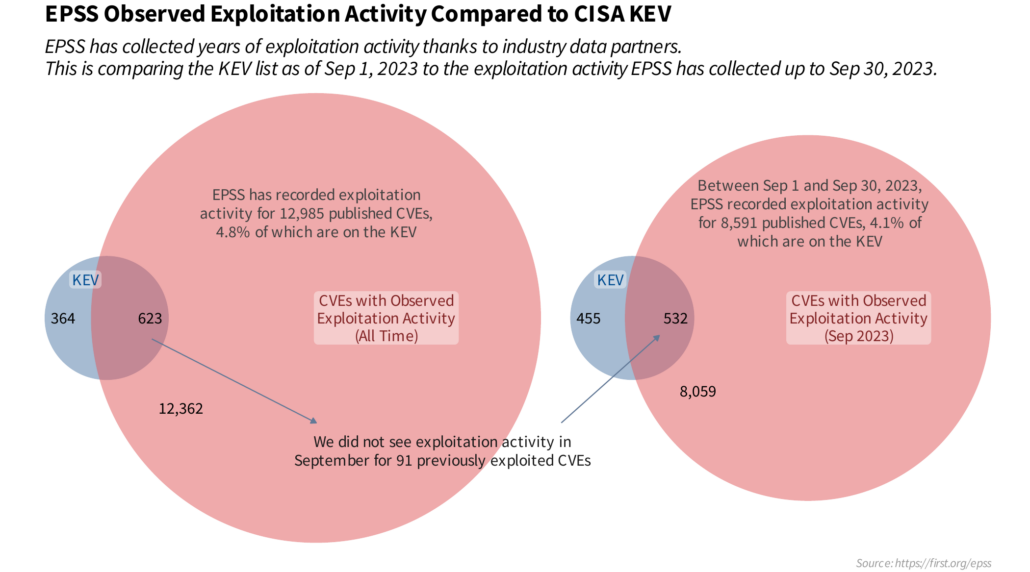
I took some time to dive into the exploitation activity EPSS has recorded both historically (all time), and specifically looking at the month of Sep 2023. Notice how there are just under a 100 CVEs on the KEV list that were exploited at some point historically but that we didn’t see exploited anymore in September? That’s part of the temporal aspect we need to pay attention to and EPSS attempts to account for. It can be important to know “this has been exploited at some time”, but it’s a lot better to know “this is still being exploited” or better yet, “This is more likely to be exploited in the future” so we can get ahead of the attackers.
Note that EPSS relies on industry partners, (Fortinet, GreyNoise Intelligence, The Shadowserver Foundation, F5, Efflux, AlienVault and Cisco) and does not curate any of our own exploitation activity. If you want more information, there are a lot more detail on many aspects of EPSS in our most recent paper. This is part of some ongoing research we are doing in EPSS about how EPSS can interoperate with other standards and data sources. What are your thoughts on this?

Leave a Reply
Want to join the discussion?Feel free to contribute!