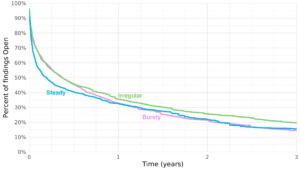
This figure shows three different survival curves. One for applications with a steady scanning cadence, one for applications with an irregular scanning cadence and one for applications with a bursty scanning cadence. Initially steady scanning reduces flaws more quickly and completely, but eventually Bursty scanning has roughly the same outcome. Irregular scanning closes fewer flaws.
© Copyright 2024 Cyentia Institute

Leave a Reply
Want to join the discussion?Feel free to contribute!