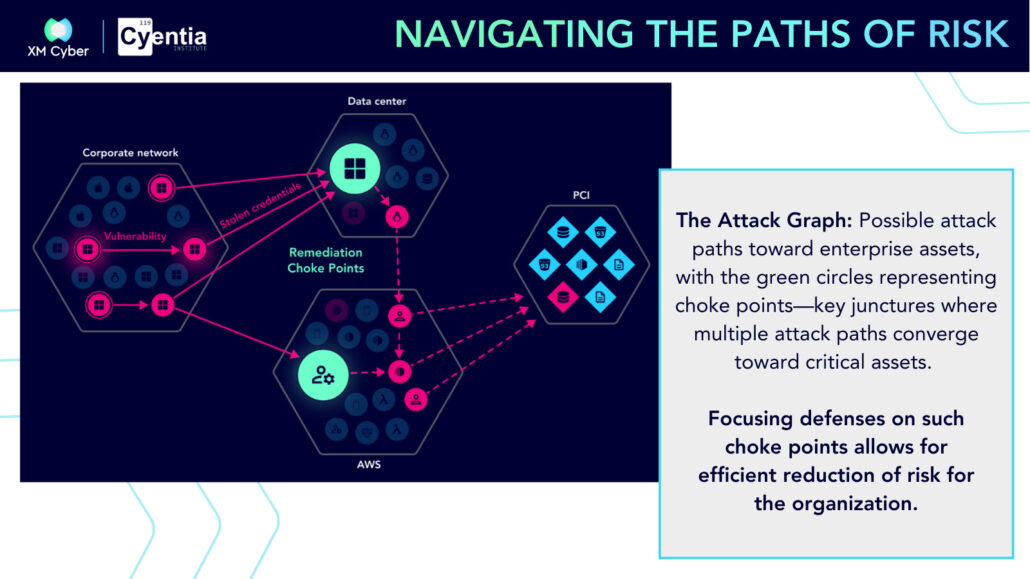
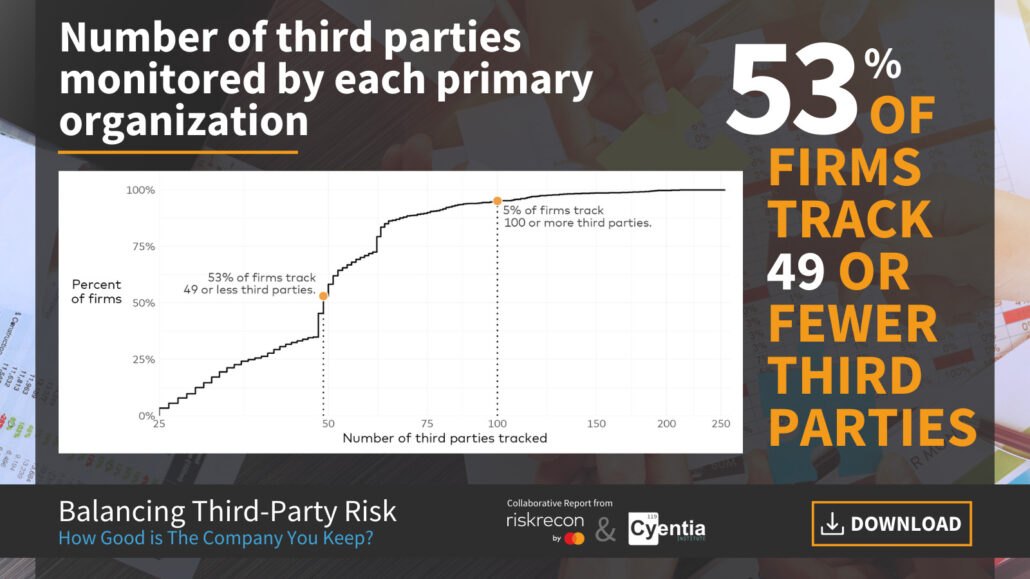
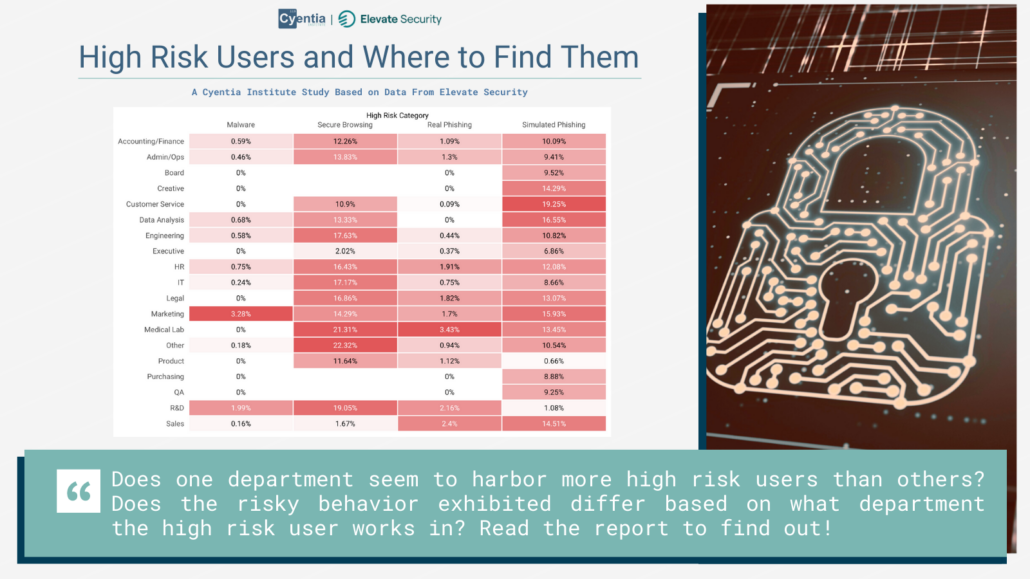
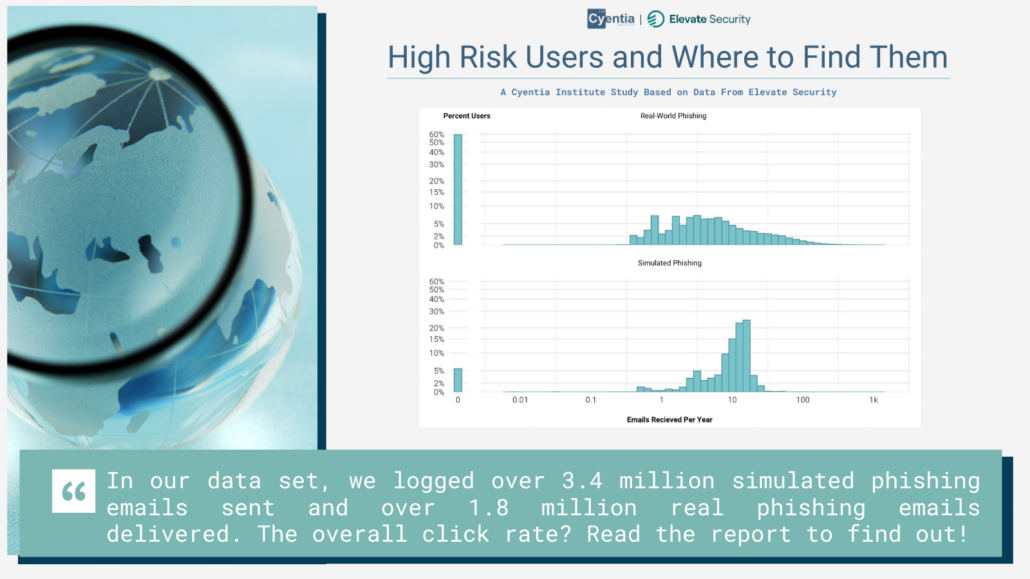
A Decade of Data-Driven Insights
Imagine having access to a comprehensive dataset spanning a decade, providing invaluable insights into the frequency and impact of common threat scenarios, actors, and techniques. That’s precisely what IRIS Risk Retina® Threat Event Analysis brings to the table. In collaboration with Advisen, a trusted leader in cyber loss data, Cyentia Institute delves into historical threat events to offer a meticulous and data-driven view of cybersecurity incidents.
Demystifying Cybersecurity
“Our goal is to offer a clearer, more data-driven perspective to support cyber risk assessments,” says the Cyentia Institute. “We recognize that threat event analysis is frequently obscured by hyperbole. With IRIS Risk Retina® Threat Event Analysis, we aim to demystify this critical aspect of cybersecurity.”
A Powerful Partnership
To ensure utmost accuracy and comprehensiveness, Cyentia Institute leverages Advisen’s Cyber Loss Data. This dataset comprises a staggering 150,000 historical cyber events collected from publicly verifiable sources, making it the most comprehensive incident dataset available. Cyentia Institute complements this data with supplemental research, cutting-edge data science techniques, and cybersecurity expertise, resulting in extensive analysis presented in Risk Retina.
Illuminating Insights
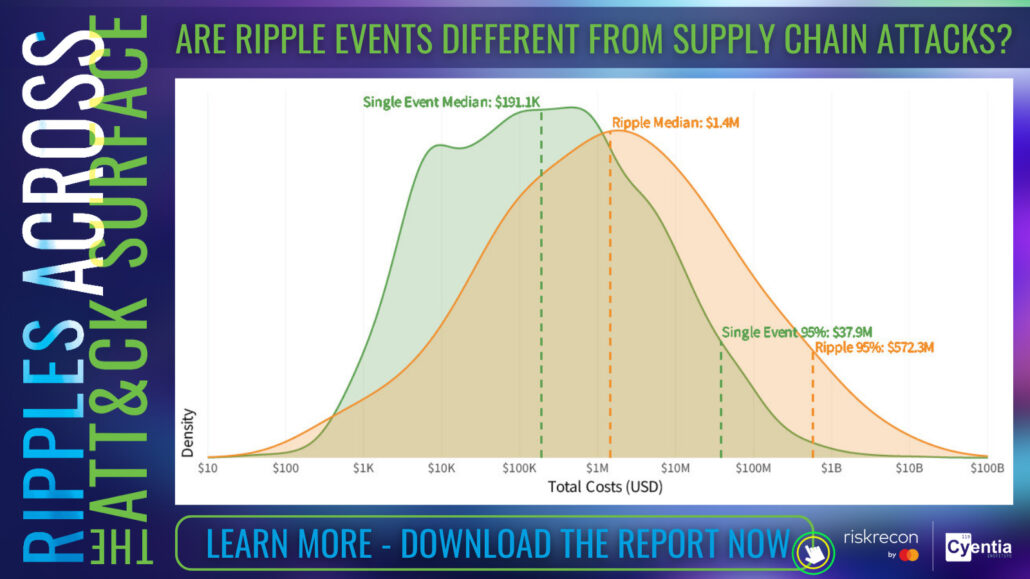
IRIS Risk Retina® Threat Event Analysis offers a detailed exploration of incident patterns, threat actors, financial impacts, actor trends across sectors and sizes, threat actor varieties, threat actions (including ATT&CK TTPs), VERIS Action Categories, ATT&CK Tactics & Techniques, top initial access techniques, post-compromise techniques, data exfiltration and impact techniques, compromised assets and attributes, and much more.