Nope; that’s not a misspelling. Perhaps we’ll fully solve the persistent problem of human risk in cybersecurity one day, but until then, we’re forced to find ways to salve its effects. And since humans are complicated, that task is also complicated. Which is why I’m pleased to see a company like Elevate Security using a bunch of relevant data to study and mature human risk management.
A while back I posted on LinkedIn asking people for opinions on topics they’d like to see the Cyentia Institute research in the future. The most common response was something related to human risk, an area we (until recently) haven’t touched on at all. That changed when the folks at Elevate saw the thread and reached out saying they have interesting data on the topic. After some exploratory analysis of that data, we heartily agreed, and a joint study titled “Elevating Human Attack Surface Management” was born.
This first-of-its-kind study aggregates data from the Elevate Security platform spanning 114,000 end users across 2,000 organizational departments between 2018 and 2020. We highlight key lessons to be learned from the data about measuring and managing the human attack surface. There’s no way to get into all that in this post, but I do want to highlight a couple charts illustrating why this complex topic needs more hard data and good research.
There’s a lot of research in the social sciences about individualism vs collectivism. I find human risk fascinating because such a crazy mix (mess?) of individual and group dynamics. Since phishing is top of mind for human risk and is one of the earliest detectable actions in the chain of events leading to security incidents, let’s use that as an example. Have you ever wondered why cyber threat actors, from bottom-rung criminals to upper- tier national military units, incorporate phishing into their tactics, techniques, and procedures (TTPs)? The chart below illustrates the answer more clearly than the savviest cyber threat intelligence analyst ever could: because it works.
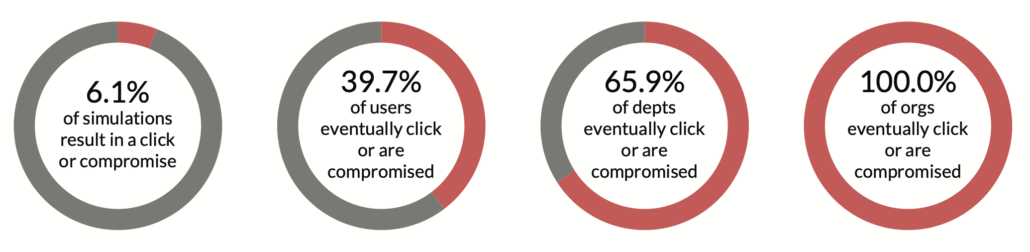
Many organizations run simulated exercises to raise awareness and strengthen resistance to phishing. In isolation, these phishing simulations offer some encouragement; only 6% result in users getting hooked. However, across multiple simulations, the encouraging signs begin to wane as almost 40% of users fall for the phish. If we continue rolling results up the organizational hierarchy, two-thirds of departments get duped. And when we evaluate click rates across the entire organization, we see that it is certain someone eventually will take the bait.
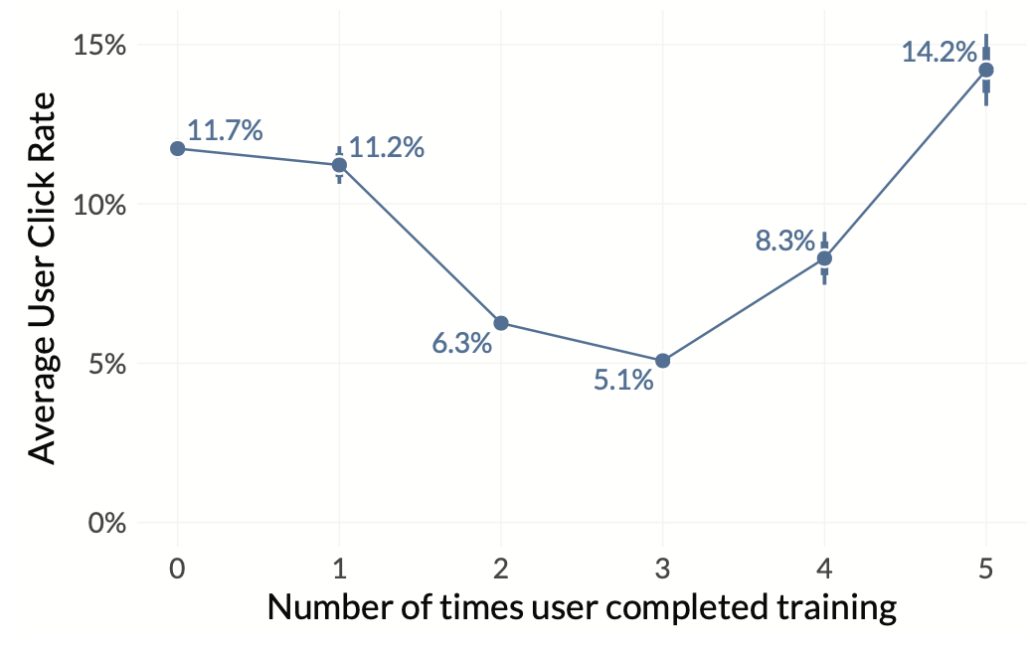
Training is a common tool for organizations hoping to curb click-happy employees. But do those lessons stick? The chart below offers a reason to take hope as well as take heed. The phishing click rates among users with three rounds of training (5%) drop to less than half that of untrained employees (12%). So far, so good. But as simulations and training pile up, we never get to a zero click rate. In fact, users with five training sessions are actually more likely to click than those with little to no training! Seems like over-training is an issue for human learning as well as for machine learning.
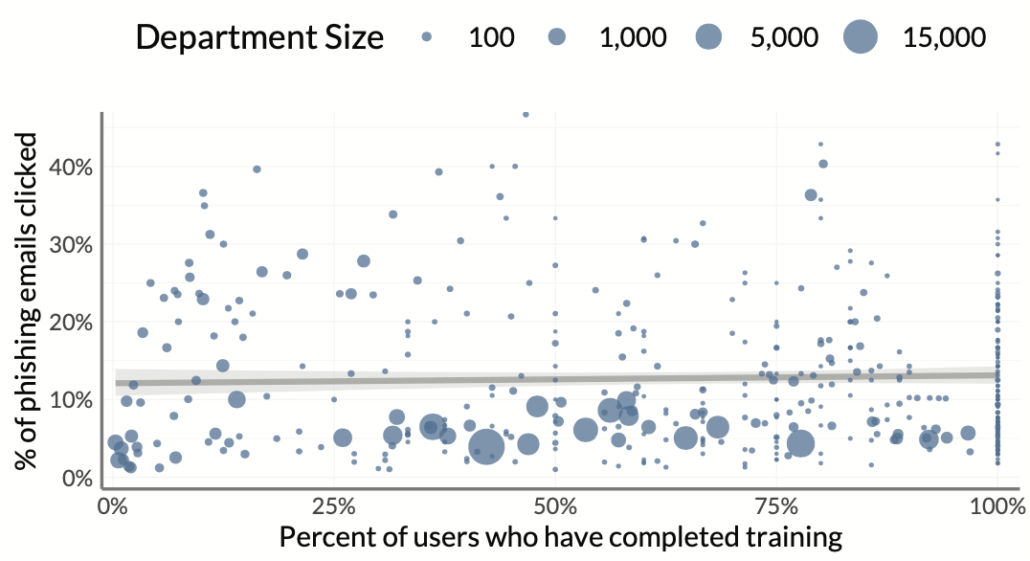
Think of the chart below as the collectivist version on the one above for individual users. Each dot represents an organizational department and the position along the vertical axis indicates the percentage of users in each department that clicked on a phishing email. The chart on the left shows the effect of training pervasiveness on click rates. As you might infer from the flat regression line and the random scattering of dots across the plot, the effect is not significant. In other words, pushing for 100% security training compliance won’t solve your firm’s phishing problem (by itself).
Looking for other examples to salve human risk in your organization? Wondering how various interventions affect behaviors beyond clicking on phishing emails? Curious to know whether your employees or your bosses are more prone to risky actions? Great – you’ll find all that and more in the full report! I’d also like to mention that I’m having a chat with Elevate’s CEO, Robert Fly, on July 15 about this topic/research. Please consider joining in with us for the discussion.



Leave a Reply
Want to join the discussion?Feel free to contribute!