/wp-content/uploads/2024/03/Screenshot-2024-03-15-at-11.43.05 AM.png
681
1920
Carolyn Gimarelli
/wp-content/uploads/[email protected]
Carolyn Gimarelli2024-03-22 02:30:512024-03-29 12:56:15Championing Cybersecurity Progress: How You Can Contribute
/wp-content/uploads/2024/03/FeaturedImageGraphic.jpg
900
1600
Carolyn Gimarelli
/wp-content/uploads/[email protected]
Carolyn Gimarelli2024-03-07 12:00:122024-03-29 13:22:40Addressing Cybersecurity's Top Challenges & Providing Unique Advantages
/wp-content/uploads/[email protected]
0
0
Carolyn Gimarelli
/wp-content/uploads/[email protected]
Carolyn Gimarelli2024-02-22 12:00:582024-02-09 17:52:32Mastering Cyber Risk: Strategies for a Secure Future
/wp-content/uploads/2024/02/Diagnosis-Cyber-Attack-Rx-IRIS-Risk-Retina-for-the-Healthcare-Sector.jpg
900
1600
Carolyn Gimarelli
/wp-content/uploads/[email protected]
Carolyn Gimarelli2024-02-15 12:00:232024-02-15 10:35:15Enhanced Marketing Strategies: Cyentia's Insights for Healthcare and Recent Cybersecurity Incidents
/wp-content/uploads/2023/11/TidalCyber-Chart-1.jpg
900
1600
Carolyn Gimarelli
/wp-content/uploads/[email protected]
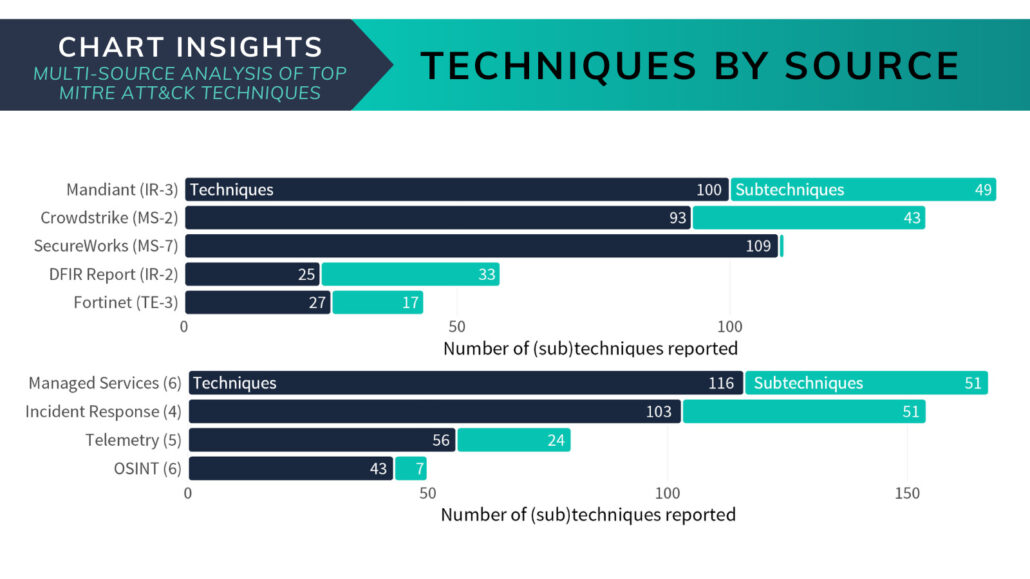
Carolyn Gimarelli2024-02-12 12:00:412024-02-12 19:55:13Transforming Cyber Threat Intelligence into Security Action with MITRE ATT&CK
/wp-content/uploads/2023/09/HeathcareRR_TransparentBkg.png
1920
1768
Carolyn Gimarelli
/wp-content/uploads/[email protected]
Carolyn Gimarelli2024-01-23 20:01:272024-03-29 12:58:18Cyber Risk in Healthcare: A Comprehensive Analysis with IRIS Risk Retina for the Healthcare Sector
/wp-content/uploads/2023/07/SSC-AVD-KF-1.jpg
900
1600
Carolyn Gimarelli
/wp-content/uploads/[email protected]
Carolyn Gimarelli2023-12-22 19:58:312023-12-22 20:00:562023 Highlights! A Year in Review
/wp-content/uploads/2023/12/RR-NthParty-INTRO.jpg
900
1600
Carolyn Gimarelli
/wp-content/uploads/[email protected]
Carolyn Gimarelli2023-12-13 12:48:332023-12-13 12:51:40Enhance Your Risk Management: Exploring Nth-Party Complexities in Our Latest Report
/wp-content/uploads/2023/12/SantaReadingTEA.jpg
512
512
Carolyn Gimarelli
/wp-content/uploads/[email protected]
Carolyn Gimarelli2023-12-10 12:15:512023-11-21 12:24:53Santa's Data Breach Debacle
/wp-content/uploads/2023/11/Screenshot-2023-11-29-at-9.07.24 AM.jpg
524
1254
Carolyn Gimarelli
/wp-content/uploads/[email protected]
Carolyn Gimarelli2023-12-01 12:15:352023-11-29 12:19:20Demystifying Data: Dive into Cyentia's Research Library
© Copyright 2024 Cyentia Institute
Scroll to top